Someone is targeting Roblox developers with info-stealing malware
An unknown party has been targeting developers of the popular online game Roblox, seeding more than a dozen open-source software packages they use with information-stealing malware called “Luna Grabber.”
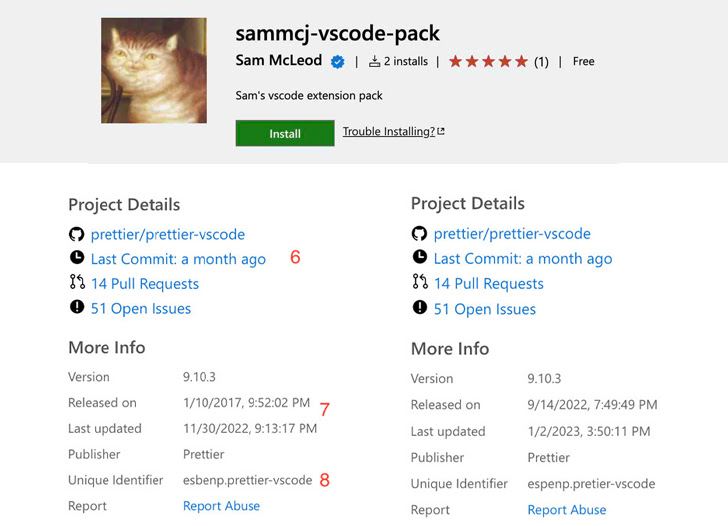
The campaign, discovered by researchers at ReversingLabs, uses typo-squatting and a number of sophisticated obfuscation tactics to entice users into downloading fake versions of commonly used software on npm, a popular open source software library. While in many cases those packages still contain the legitimate code developers are looking for, they also include a multi-stage malware attack that can deploy Luba Grabber on a victim’s web browser, their Discord application and other sources.
The malware was initially discovered as part of ReversingLabs “routine monitoring” of npm, identifying one such package called noblox.js-vps that was “clearly typo-squatting” the name of a legitimate Roblox API wrapper. In a post published Tuesday, threat researcher Lucija Valentić wrote that the stolen information could potentially be leveraged in future attacks.
“The use of the Luna Grabber ‘turnkey’ open source malware [can] generate malicious executables that act as bait in phishing and supply chain attacks, gathering sensitive information from targeted developers,” wrote Valentić.
Npm is one of the largest open source software repositories in the world, but the observed impact of the campaign thus far has been muted compared with other open source campaigns: just under 1,000 users have downloaded the infostealer across more than a dozen discovered software packages. Many of the identified packages have since been removed, but ReversingLabs noted the campaign remains ongoing.
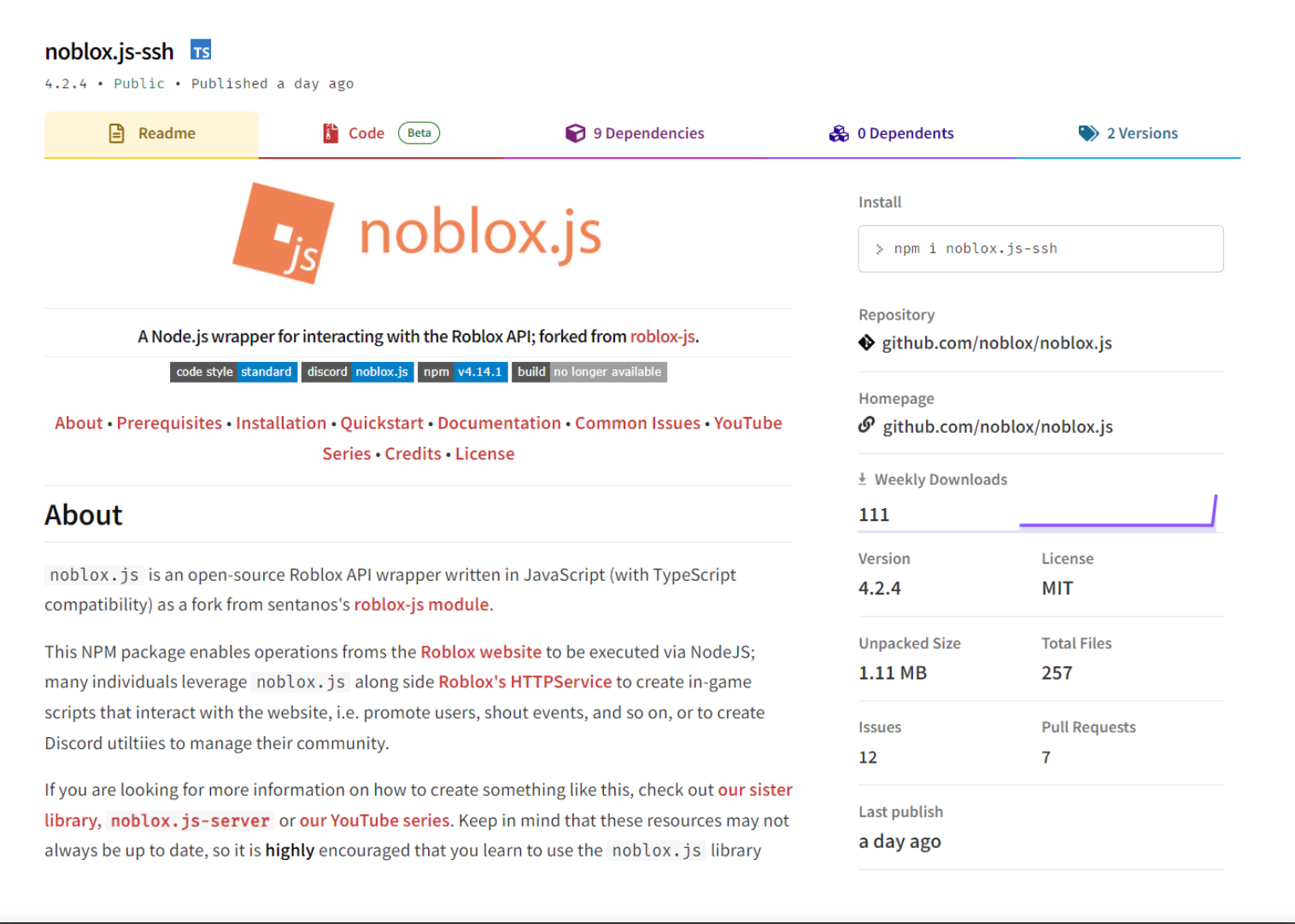
Roblox is an online video game platform where, similar to games like Minecraft, users can build virtual worlds and levels for others to play in. Since the COVID-19 pandemic, its popularity has exploded: according to data analytics reporting firm DemandSage, the game currently boasts more than 66 million daily active users and 214 million monthly active users.
It’s not…