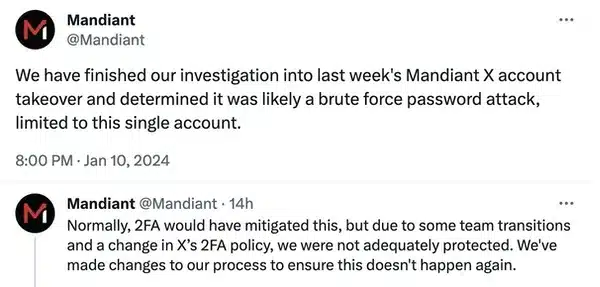
Security firm now says toothbrush DDOS attack didn’t happen, but source publication says company presented it as real
Update 2 — 2/9/2024 6:30am PT: The security company at the nexus of the original report that three million toothbrushes were used in a DDOS attack has now retracted the story and claimed it was a result of a mistranslation — but according to the news outlet that published the initial report, that statement isn’t true. The reports of this story are not based on a mistranslation by the media. The publication claims Fortinet presented the story as having actually happened and approved the text of the article, which had been submitted to Fortinet prior to publication.
Here’s the Aargauer Zeitung’s (the source of the story) statement on the matter (via Google Translate):
What the Fortinet headquarters in California is now calling a “translation problem” sounded completely different during the research: Swiss Fortinet representatives described the toothbrush case as a real DDoS at a meeting that discussed current threats -Attack described.
Fortinet provided specific details: information about how long the attack took down a Swiss company’s website; an order of magnitude of how great the damage was. Fortinet did not want to reveal which company it was out of consideration for its customers.
The text was submitted to Fortinet for verification before publication. The statement that this was a real case that really happened was not objected to.
Fortinet’s global management has now backtracked on its statement, which was sent to various international media outlets. The company also failed to send this to CH Media. We have not yet received any further statements from Fortinet.”
EDIT 2/7/2024 — 3:30pm PT: Fortinet sent us a statement indicating that the report of the toothbrush attack is inaccurate:
“To clarify, the topic of toothbrushes being used for DDoS attacks was presented during an interview as an illustration of a given type of attack, and it is not based on research from Fortinet or FortiGuard Labs. It appears that due to translations the narrative on this topic has been stretched to the point where hypothetical and actual scenarios are blurred.” – Fortinet.
The original text of the source report read:
“She’s in the bathroom at home, but she’s part of a large-scale cyber…