Advanced Insights into Digital Credentials to Fortify Internet Security
As we navigate the complex landscape of the digital realm, the importance of securing all our online interactions has become paramount. The exchange of sensitive information and execution of financial transactions underscore the critical need for advanced digital security measures.
Digital credentials are at the forefront of establishing digital trust—a concept we have delved into previously in ‘The Evolution of Digital Trust’. In this blog, we zero in on the role of digital credentials within Transport Layer Security (TLS), supported by Public Key Infrastructure (PKI), which has been a fundamental aspect of internet security for over three decades.
In today’s AI-driven era, fostering trust in digital transactions and interactions presents a unique set of challenges. With cyber threats rapidly evolving and on the rise, the urgency to adopt advanced security frameworks has never been more acute, necessitating a proactive approach to safeguard our digital interactions and ecosystem.
Client-Server and The Man-in-the-Middle
Long before the evolution of the modern internet as we know it today, security and privacy in digital transactions were of paramount concern. This was the era of Web 1.0, the first version of the internet, where digital users were merely consumers of information; web developers were the only content creators, and ubiquitous ‘http’ protocol governed browser addresses.
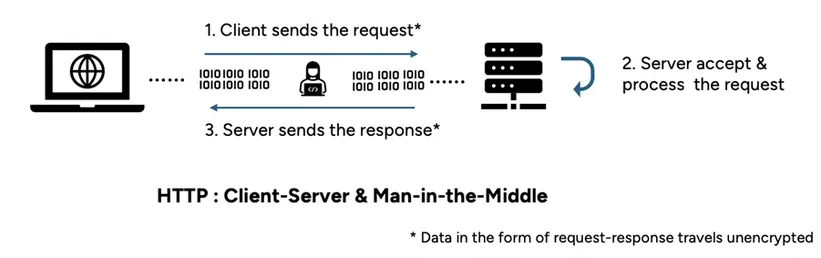
In the traditional client-server communication model, powered by http, anyone with basic networking tools can decipher every bit of the un-encrypted interaction between a browser (i.e. client) and the website (i.e. server). Fortunately, browsers ensure that users are cautioned that such interactions are not innately secure.

Client-Server and HTTPS
It did not take long before Netscape, in 1995, introduced Hyper Text Transfer Protocol Secure (HTTPS), which was HTTP secured by SSL 2.0 – a cryptographic protocol that provided end-to-end communication security over networks. This protocol has evolved significantly since then and is now known as TLS (Transport Layer Security), with the most recent version being TLS 1.3.
When you visit a…





