How To Easily Fix Avast Not Working on Mac
As Mac owners, we often hear about the importance of security software in protecting our data and privacy. Avast is a popular antivirus software choice for Mac owners, but what happens when it is not working anymore? In this article, we will explore the issues you may encounter with Avast on Mac and solutions for resolving them.
Does Avast Work on Macs?
Yes, Avast does work on Macs. It is a well-known antivirus program designed to protect computers from malware and other security threats. Avast offers a range of products for Mac, including Avast Security for Mac which provides protection against viruses, ransomware, and other malware threats, and Avast Premium Security which adds additional features like Wi-Fi intruder alerts and ransomware protection.
What To Do if Avast Is Not Working on Mac?
If you find that Avast is not working on your Mac, there may be a compatibility issue between the version of macOS you are running and the version of Avast installed. Here’s how to update your macOS and Avast:
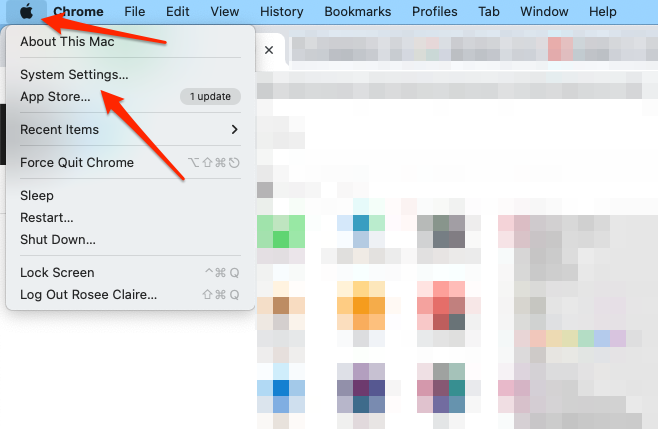
- Click on the Apple menu > System Settings.
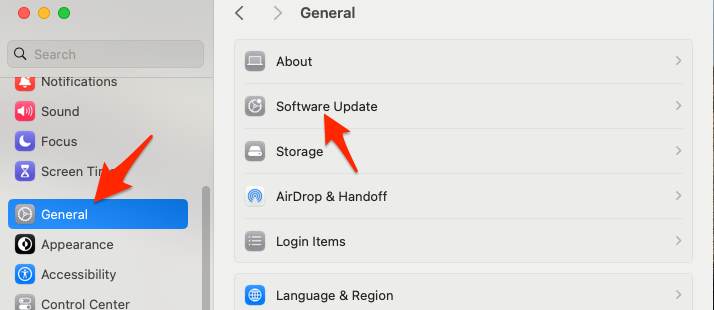
- Click on General > Software Update.
- If an update is available, click on Download and Install and follow the on-screen instructions.
- To update Avast open Avast Security then go to Menu > Preferences and click Update Now.
After updating macOS, check if Avast is working properly.
Does Mac Recommend Antivirus?
Apple has often been known to suggest that its macOS is secure and does not necessarily require an antivirus. However, in reality, no system is immune to threats. An additional layer of security is never a bad idea. As the number of Mac users grows, so does the interest of cybercriminals in targeting this platform. Moreover, even your iPhone and iPad can use an extra layer of protection.
While Avast is a reputable antivirus program, it is not the only option for Mac users. One notable alternative worth considering is Intego Internet Security. The antivirus is built exclusively for Mac, which means that its developers focus solely on Mac security. This specialization allows Intego to offer features finely tuned to the macOS environment.
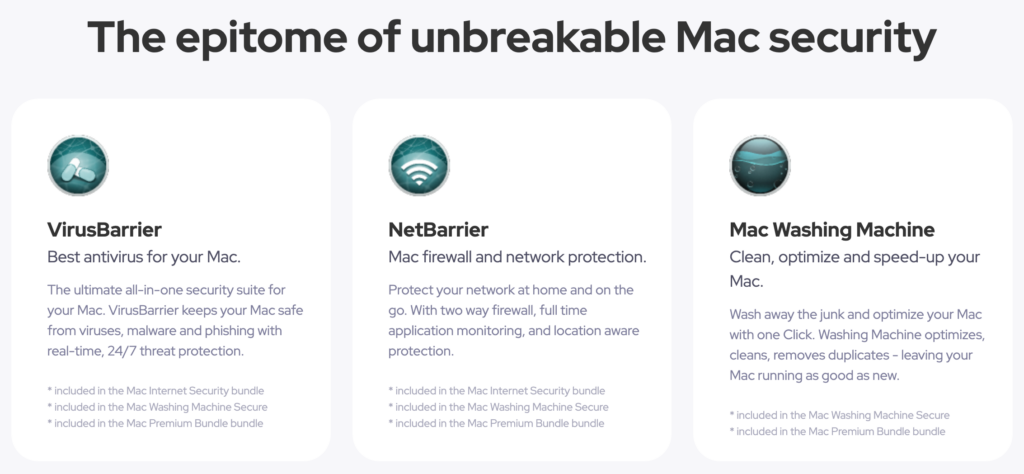
Intego Internet Security offers a suite of tools, including VirusBarrier (antivirus protection),…