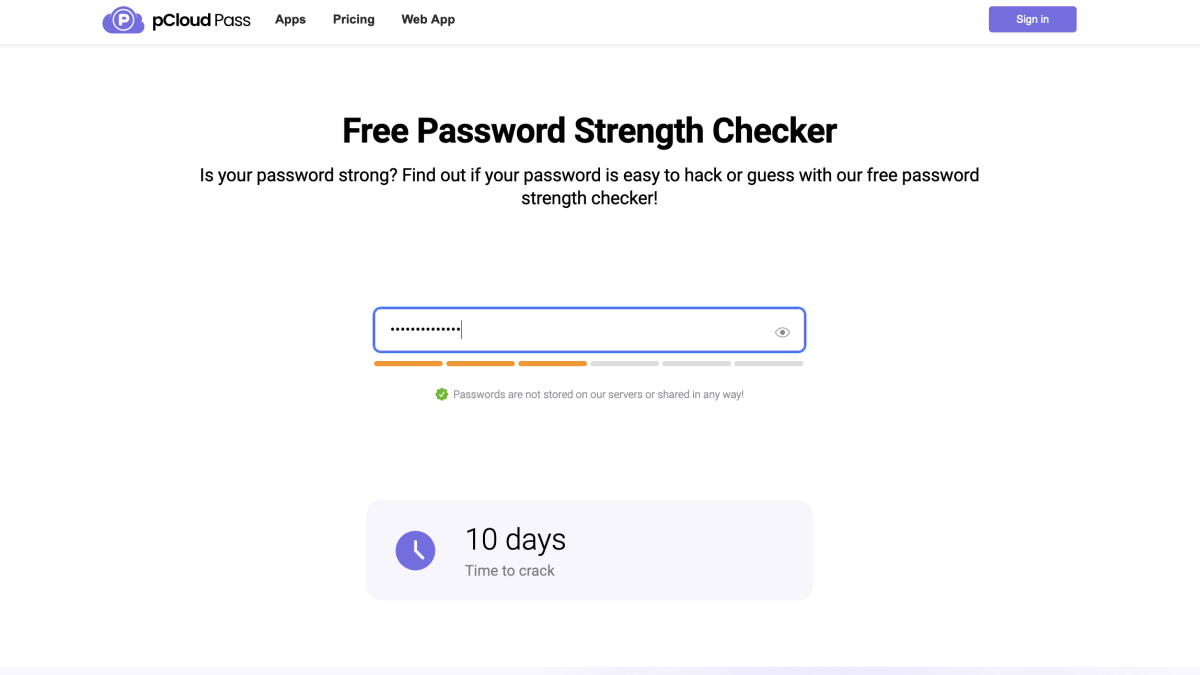
2,430 hacking crimes investigated; 7,092 suspects arrested since 2022, effectively safeguarding cybersecurity: public security authority

Photo: VCG
Since 2022, public security organs across China have investigated 2,430 hacking crimes and arrested 7,092 suspects, effectively cutting off the chain of hacking crimes, protecting network and data security, and safeguarding the normal order of cyberspace, the Ministry of Public Security announced on Thursday at a press conference.
The authority noted that according to its latest statistics, the number of hacking cases in China has been increasing for three consecutive years, with an average annual growth rate of 27.7 percent. The ministry also noted that the average age of hackers has been decreasing year by year, and there have even been cases of elementary school students proficiently using hacker tools.
The rise in hacking crimes has become increasingly prominent in recent years. During the press conference in Beijing, Shi You, the deputy director of the Bureau of Network Security Protection of the ministry, introduced that hacking crimes mainly involve illegal intrusion into computer information systems, unauthorized access to computer data, illegal control of computer information systems, providing programs and tools for illegal intrusion and control of computer information systems, as well as the destruction of computer information systems.
The ministry released 10 typical cases of hacker crimes, as part of the efforts and significant achievements by the authority during the nationwide campaign called “Clean up the Internet.”
In one typical hacking case, the Panzhihua public security bureau in Southwest China’s Sichuan Province successfully handled in January a case of making profit through illegal remote manipulation of older mobile phones, with the whole chain making illegal profits of more than 100 million yuan ($14.02 million).
The local public security authority in September 2022 uncovered multiple cases of automatic ordering of value-added services on older phones, resulting in monthly deductions of 1 to 10 yuan ($1.4) for related value-added services, indicating that the phones were remotely controlled.
After investigation, it was found that the suspects surnamed Chen and Gao colluded with vendors and manufacturers of older phones to implant Trojan programs…