Chinese Experts Uncover Details of Equation Group’s Bvp47 Covert Hacking Tool
Researchers from China’s Pangu Lab have disclosed details of a “top-tier” backdoor put to use by the Equation Group, an advanced persistent threat (APT) with alleged ties to the cyber-warfare intelligence-gathering unit of the U.S. National Security Agency (NSA).
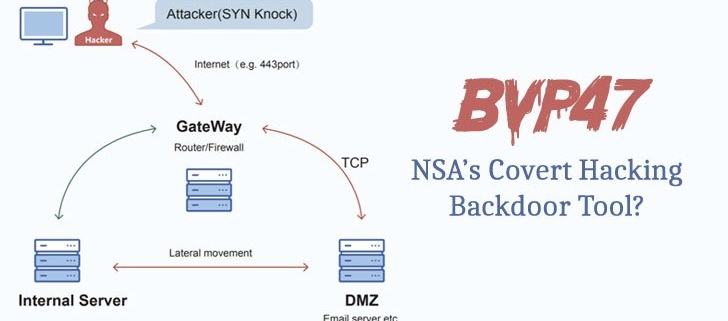
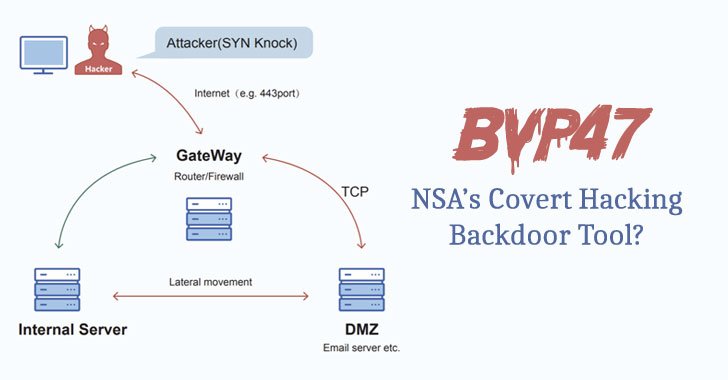
Dubbed “Bvp47” owing to numerous references to the string “Bvp” and the numerical value “0x47” used in the encryption algorithm, the backdoor was extracted from Linux systems “during an in-depth forensic investigation of a host in a key domestic department” in 2013.
Pangu Lab codenamed the attacks involving the deployment of Bvp47 “Operation Telescreen,” with the implant featuring an “advanced covert channel behavior based on TCP SYN packets, code obfuscation, system hiding, and self-destruction design.”
The Shadow Broker leaks
Equation Group, dubbed the “crown creator of cyber espionage” by Russian security firm Kaspersky, is the name assigned to a sophisticated adversary that’s been active since at least 2001 and has used previously undisclosed zero-day exploits to “infect victims, retrieve data and hide activity in an outstandingly professional way,” some of which were later incorporated into Stuxnet.
The attacks have targeted a variety of sectors in no less than 42 countries, including governments, telecom, aerospace, energy, nuclear research, oil and gas, military, nanotechnology, Islamic activists and scholars, media, transportation, financial institutions, and companies developing encryption technologies.
The group is believed to be linked to the NSA’s Tailored Access Operations (TAO) unit, while intrusion activities pertaining to a second collective dubbed Longhorn (aka The Lamberts) have been attributed to the U.S. Central Intelligence Agency (CIA).
Equation Group’s malware toolset became public knowledge in 2016 when a group calling itself the Shadow Brokers leaked the entire tranche of exploits used by the elite hacking team, with Kaspersky uncovering code-level similarities between the stolen files and that of samples identified as used by the threat actor.
Bvp47 as a covert backdoor
The incident analyzed by Pangu Lab comprises two internally compromised servers, an email and an enterprise server named V1…