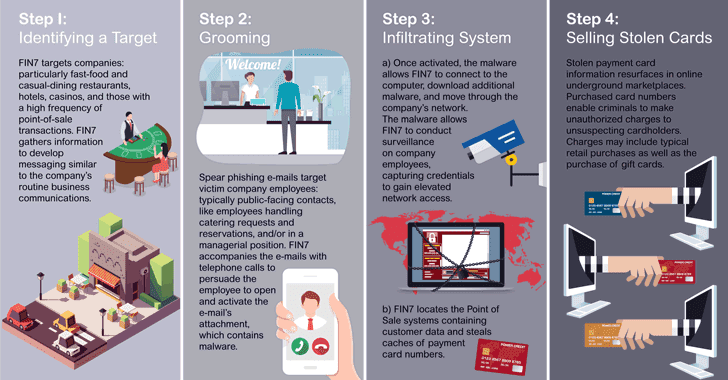
Notorious Cyber Gang FIN7 Returns With Cl0p Ransomware in New Wave of Attacks
The notorious cybercrime group known as FIN7 has been observed deploying Cl0p (aka Clop) ransomware, marking the threat actor’s first ransomware campaign since late 2021.
Microsoft, which detected the activity in April 2023, is tracking the financially motivated actor under its new taxonomy Sangria Tempest.
“In these recent attacks, Sangria Tempest uses the PowerShell script POWERTRASH to load the Lizar post-exploitation tool and get a foothold into a target network,” the company’s threat intelligence team said. “They then use OpenSSH and Impacket to move laterally and deploy Clop ransomware.”
FIN7 (aka Carbanak, ELBRUS, and ITG14) has been linked to other ransomware families such as Black Basta, DarkSide, REvil, and LockBit, with the threat actor acting as a precursor for Maze and Ryuk ransomware attacks.
Active since at least 2012, the group has a track record of targeting a broad spectrum of organizations spanning software, consulting, financial services, medical equipment, cloud services, media, food and beverage, transportation, and utilities.
Another notable tactic in its playbook is its pattern of setting up fake security companies – Combi Security and Bastion Secure – to recruit employees for conducting ransomware attacks and other operations.
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Deception can detect advanced threats, stop lateral movement, and enhance your Zero Trust strategy. Join our insightful webinar!
Last month, IBM Security X-Force revealed that members of the now-defunct Conti ransomware gang are using a new malware called Domino that’s developed by the cybercrime cartel.
FIN7’s use of POWERTRASH to deliver Lizar (aka DICELOADER or Tirion) was also highlighted by WithSecure a few weeks ago in connection with attacks exploiting a high-severity flaw in Veeam Backup & Replication software (CVE-2023-27532) to gain initial access.
The latest development signifies FIN7’s continued reliance on various ransomware families to target victims as part of a shift in its monetization strategy by pivoting away from payment card data theft to…