Finland Fending Off FluBot Malware, Again
The Finnish National Cyber Security Centre (NCSC-FI) has issued a warning to citizens about the current version of the FluBot malware campaign which is affecting “tens of thousands of people in Finland.”
The malware campaign leverages SMS by sending out numerous text messages, according to NCSC-FI. The messages, all of which are written in Finnish, use different verbiage.
A telltale way to identify the messages as illegitimate is to look at the alphabet used in the creation of the messages; they are missing certain Scandinavian letters (å, ä and ö) and include symbols in odd places. The analysis by the NCSC-FI is that the insertion of these symbols is by design—to make it difficult for telecom operators to filter out the FluBot SMS messages.
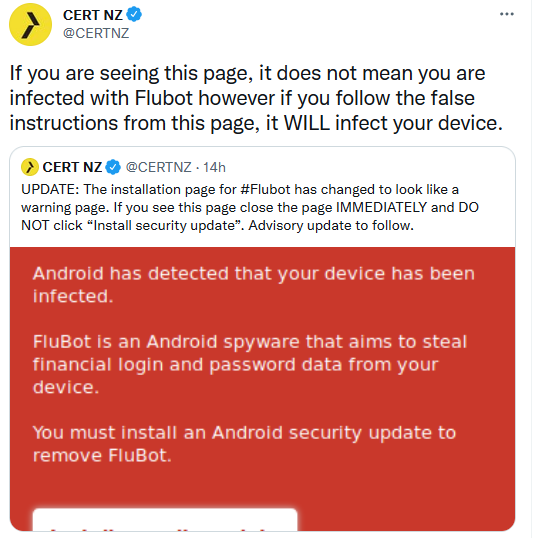
While the individual message text may vary, the underlying theme and the socially engineered “hook” is that the recipient has received a voicemail. Clicking on an included link will prompt them to allow installation of an app onto their device to listen to the fake voicemail; if they allow it, the malware is then installed.
The NCSC-FI advises that the malware, once in place, steals the individual’s data and also sends additional “malware-spreading scam messages.”
Déjà FluBot
This is not the first instance of the FluBot malware appearing in Finland. The June 2021 campaign saw thousands of victims falling for the scam. Back in June, the hook was that the recipient had a “package awaiting delivery” and the link ostensibly took the user to a package tracking site.
The current campaign is targeting Android devices with a mobile subscription from a local telecommunications operator. Apple device owners are redirected to another website controlled by the cybercriminals.
Antti Turunen, head of anti-fraud at Telia, said this instance of FluBot is worse than the summer campaign. Teemu Makela, chief information security officer (CISO) at Elisa Oyj, added, “The malware attack is highly unusual and very alarming. A significant number of text messages are passing through. It is estimated [that] millions of SMS messages are passing through the various mobile service providers with Telia indicating it had intercepted several hundred…