Calendar app gaining popularity with students raises security concerns
COLORADO SPRINGS — A popular app used by high schoolers is raising concerns from parents and cybersecurity experts. The Saturn app is promoted as a way for high school students to view their schedule, chat, and create a social calendar for meeting up, and planning for school events.
Just two weeks ago, concerns were raised by parents over the ability to link to a user’s TikTok, Snapchat, and other social media accounts.
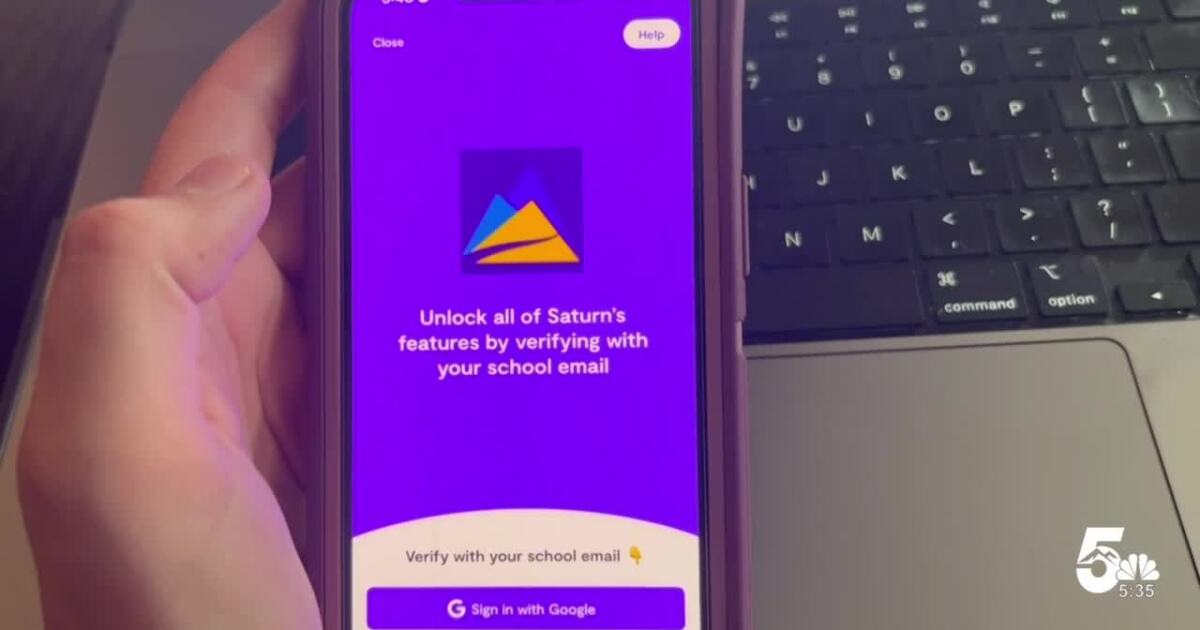
Another big concern is anyone who downloads the app can make a profile, claiming to be a student. But after reaching out to Saturn myself, I’m told the app has created major changes in the past week to increase security.
Saturn Technologies released a statement saying it is now using a verification process to make sure that those who download the app are actual students at the school they claim to be a part of. The verification process makes sure users use a school email to view class details and students’ profiles.
But a local cybersecurity expert I spoke with tells me the app still holds several red flags when it comes to security. And he doesn’t believe the app is secure enough to shy away hackers.
“Some of the dangers that you might encounter from having too much information on there is stalking, there might be stalkers out there if your location is known, you open yourself up to burglary or more serious crimes. Identity theft, data breaches, so there’s a slew of things that kids face once they get on this particular app,” said Thomas Russell, a cyber education program manager at the National Cybersecurity Center.
“Right now, I can join and easily mock some type of school email because I know the patterns of the school emails locally, and I can easily go in there and get an account myself. And if I can do it, that means anyone can do it.”
Thomas tells me this is a concern because your child can never know exactly who they are talking to. It’s important that parents use parental controls and look at the app and continue to monitor their child’s chat room behavior on the app.
While the app has grown in popularity in our area, it is not something local high schools are asking their students to download. I spoke with several local school…