Google reports a significant surge in zero-day vulnerabilities in 2023
A new report released today by Google LLC’s Threat Analysis Group and Google-owned Mandiant warns that zero-day exploits have become more common amid a rise in nation-state hackers.
The report, “We’re All in this Together: A Year in Review of Zero-Days Exploited In-the-Wild in 2023,” detailed 97 zero-day vulnerabilities observed by Google in 2023, up from 62 in 2023 but down from 106 in 2021. Zero-day attacks exploit a previously unknown vulnerability in software before developers have had the opportunity to fix it.
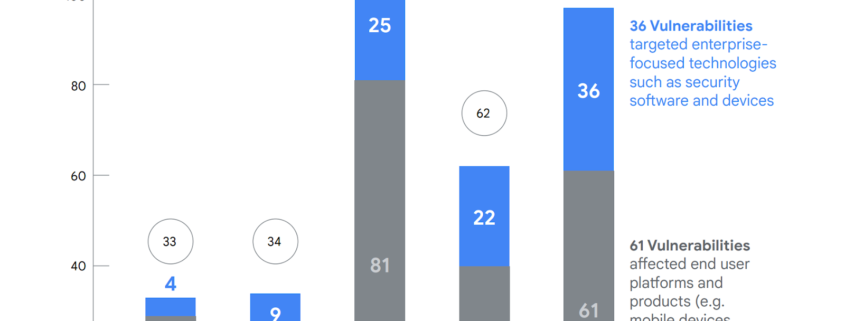
Of the 97 zero-days tracked in 2023, 36 targeted enterprise-focused technologies, such as security software and devices, while the remaining 61 affected end-user platforms and products, such as mobile devices, operating systems, browsers and other applications.
Adversary exploitation of enterprise-specific technologies jumped 64% over the previous year, with Google also seeing a general increase in the number of enterprise vendors targeted since 2019. Attackers were seen to be shifting to third-party components and libraries in 2023, as zero-day vulnerabilities in both were found to be a prime attack surface in 2023.
Commercial surveillance vendors — companies that develop and sell tools and software designed for monitoring and gathering intelligence, often used by governments — were found to be behind 75% of known zero-day exploits targeting Google products and Android ecosystem devices in 2023. CSVs were also found to be behind 60% of the 37 zero-day vulnerabilities in browsers and mobile devices exploited in 2023.
The report alleges that China was the lead source of government-back exploitation, claiming that Chinese cyber espionage groups exploited 12 zero-day vulnerabilities in 2023, up from seven in 2022.
Another finding in the report was surprising: The Google researchers found that exploitation associated with financially motivated actors proportionally decreased in 2023, with financially motivated actors found to account for only 10 zero-day exploits last year. Threat group FIN11 was found to be behind three of them.
“Exploiting zero-days is no longer a niche capability,” the report notes. “The proliferation of exploit technology…