Tag Archive for: Headache
How to comply with PSD2 authentication without a headache
/in Mobile Security
The European Union’s Payment Services Directive 2 (PSD2) regulation finally came into full force in most countries this year, putting the burden on companies to meet authentication requirements for payments. Regulations like these often come with additional security hoops consumers have to jump through. But it doesn’t have to be that way.
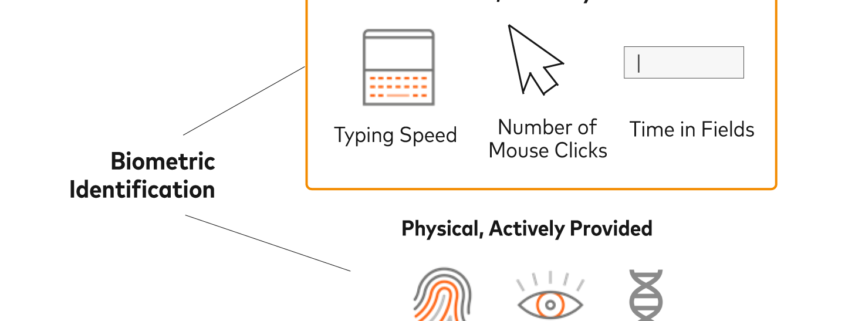
With the right strategy, companies can provide frictionless online experiences while remaining compliant with constantly changing regulations, including PSD2. Using passive behavioral biometrics, you can seamlessly verify that the right person is behind the device, meeting requirements without the need for additional authentication steps. Find that hard to believe? Well, read on.
How not to do PSD2: knowledge questions
While PSD2 has technically been on the books since September 2019, one rule didn’t actually go into effect until December 31, 2020: the requirement that payment service providers (PSPs) use Strong Customer Authentication (SCA). Using SCA means a payment must satisfy two of three authentication factors:
- Knowledge: Something the consumer knows (e.g., PIN or password)
- Possession: Something the consumer has (e.g., device or credit card)
- Inherence: Something the consumer inherently is (e.g., fingerprint or facial recognition)
To remain PSD2-compliant, many companies are using one-time passcodes (OTPs) to verify logins and payments. With OTPs, users receive a code on their device to ensure it’s in their possession — fulfilling the possession requirement for SCA. But that leaves one verification step unfulfilled. Most companies opt to have users fulfill the knowledge requirement by typing in a password. But this adds an extra step — and unnecessary friction — to the user experience.
The looming question: What will the second authentication factor be?
This is where passive behavioral biometrics comes into play by verifying user identity without the need for additional step-ups. Imagine you are logging in to your mobile banking app. When you enter the OTP code sent to your device, instead of having to manually verify your credentials a second time, there’s technology that can detect whether it’s you just by the way you…
Simpson: Hybrid warfare NATO’s next headache – The London Free Press
/in Internet SecuritySimpson: Hybrid warfare NATO’s next headache The London Free Press
“cyber warfare news” – read more
Israel’s Iron Dome Headache (As In China Might Have Stolen the Specs On It) – The National Interest Online
/in Internet SecurityIsrael’s Iron Dome Headache (As In China Might Have Stolen the Specs On It) The National Interest Online
Tiny Israel has an enormous cybersecurity industry and a deep pool of hackers and anti-hackers who learned their trade in the Israeli military. So if China can …