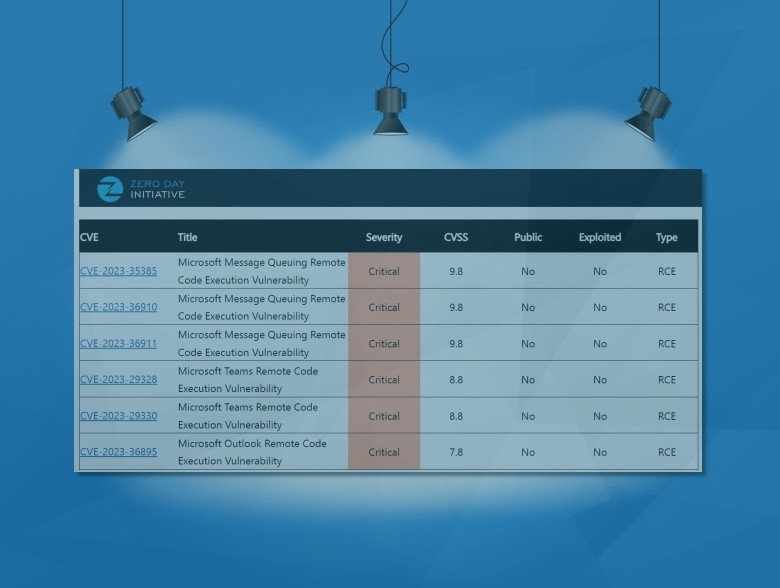
Ransomware attacks register record speeds thanks to success of infosec industry • The Register
The time taken by cyber attackers between gaining an initial foothold in a victim’s environment and deploying ransomware has fallen to 24 hours, according to a study.
In nearly two-thirds of cases analysed by Secureworks’ researchers, cybercriminals were deploying ransomware within a day, and in more than 10 percent of incidents it was deployed within five hours.
This average dwell time has dropped significantly in 2023, down from 4.5 days in 2022 and 5.5 days the year before that.
The findings remained consistent across the year’s incidents, researchers noted, not being influenced by specific ransomware variants of cybercrime groups.
Dwell times in some cases were longer when data exfiltration occurred before ransomware was deployed – a double extortion scenario.
However, this wasn’t true in every case, and as Microsoft revealed last week in its annual threat intelligence report, double extortion events accounted for just 13 percent of ransomware incidents in the past year.
Secureworks said that ransomware attacks are being carried out with less complexity than in years gone by, with the days of organization-wide encryption incidents becoming increasingly more difficult to pull off.
“The cybersecurity industry is undoubtedly getting better at detecting the activity that has historically preceded ransomware, such as the use of offensive security toolkits like Cobalt Strike,” Secureworks said in its “State of The Threat Report.”
“This may be a factor in forcing ransomware operators to work more quickly.”
As detection technologies become more effective, cybercriminals are naturally forced to adapt to a changing defensive landscape, having to complete their attacks faster.
Secureworks’ experts also said the popularity of the ransomware-as-a-service (RaaS) model could also provide an explanation for shorter attacks.
With effective ransomware payloads, complete with easy-to-follow instructions for affiliates to use them, the RaaS model makes executing attacks possible for even the least-skilled criminals.
This lowering of the barrier to enter the ransomware market as an affiliate has led to an increase in attacks overall, and June broke the single-month record for…