New 5G Modem Flaws Affect iOS Devices and Android Models from Major Brands
A collection of security flaws in the firmware implementation of 5G mobile network modems from major chipset vendors such as MediaTek and Qualcomm impact USB and IoT modems as well as hundreds of smartphone models running Android and iOS.
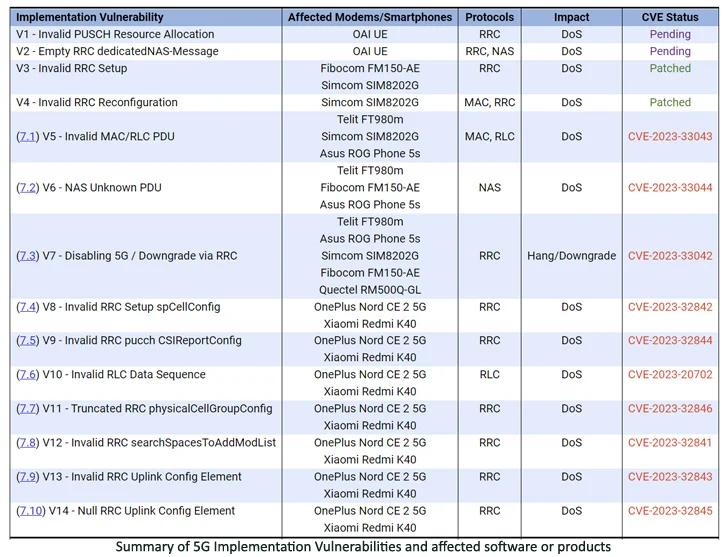
Of the 14 flaws – collectively called 5Ghoul (a combination of “5G” and “Ghoul”) – 10 affect 5G modems from the two companies, out of which three have been classified as high-severity vulnerabilities.
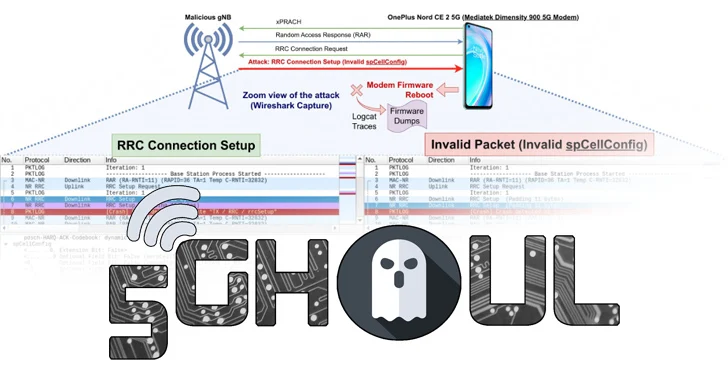
“5Ghoul vulnerabilities may be exploited to continuously launch attacks to drop the connections, freeze the connection that involve manual reboot or downgrade the 5G connectivity to 4G,” the researchers said in a study published today.
As many as 714 smartphones from 24 brands are impacted, including those from Vivo, Xiaomi, OPPO, Samsung, Honor, Motorola, realme, OnePlus, Huawei, ZTE, Asus, Sony, Meizu, Nokia, Apple, and Google.
Cracking the Code: Learn How Cyber Attackers Exploit Human Psychology
Ever wondered why social engineering is so effective? Dive deep into the psychology of cyber attackers in our upcoming webinar.
The vulnerabilities were disclosed by a team of researchers from the ASSET (Automated Systems SEcuriTy) Research Group at the Singapore University of Technology and Design (SUTD), who also previously uncovered BrakTooth in September 2021 and SweynTooth in February 2020.
The attacks, in a nutshell, attempt to deceive a smartphone or a 5G-enabled device to connect a rogue base station (gNB), resulting in unintended consequences.
“The attacker does not need to be aware of any secret information of the target UE e.g., UE’s SIM card details, to complete the NAS network registration,” the researchers explained. “The attacker only needs to impersonate the legitimate gNB using the known Cell Tower connection parameters.”
A threat actor can accomplish this by using apps like Cellular-Pro to determine the Relative Signal Strength Indicator (RSSI) readings and trick the user equipment to connect to the adversarial station (i.e., a software-defined radio) as well as an inexpensive mini…