Researchers Share New Insights Into RIG Exploit Kit Malware’s Operations
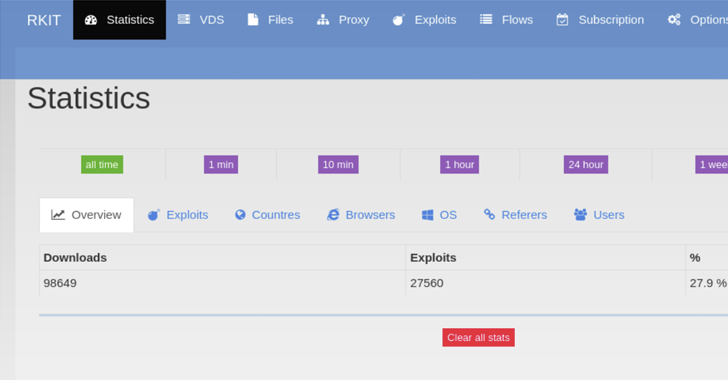
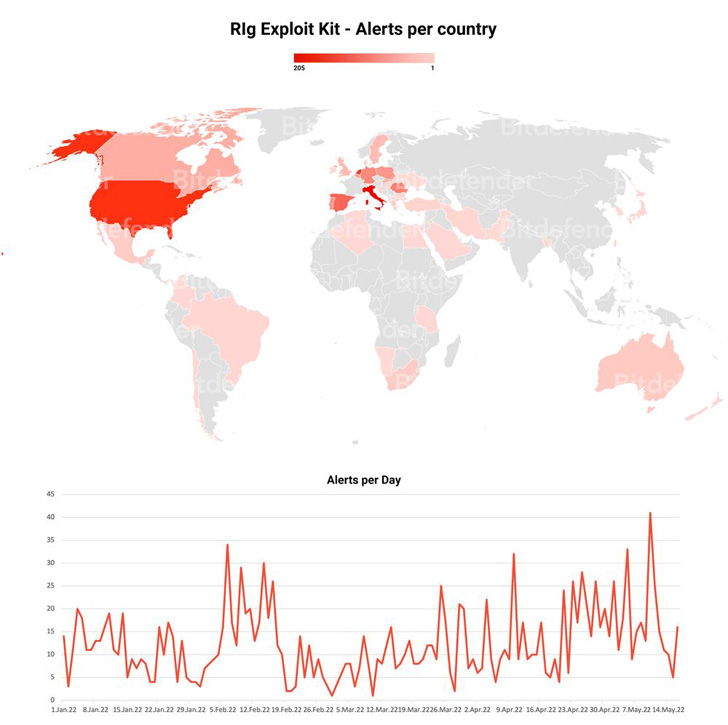
The RIG exploit kit (EK) touched an all-time high successful exploitation rate of nearly 30% in 2022, new findings reveal.
“RIG EK is a financially-motivated program that has been active since 2014,” Swiss cybersecurity company PRODAFT said in an exhaustive report shared with The Hacker News.
“Although it has yet to substantially change its exploits in its more recent activity, the type and version of the malware they distribute constantly change. The frequency of updating samples ranges from weekly to daily updates.”
Exploit kits are programs used to distribute malware to large numbers of victims by taking advantage of known security flaws in commonly-used software such as web browsers.
The fact that RIG EK runs as a service model means threat actors can financially compensate the RIG EK administrator for installing malware of their choice on victim machines. The RIG EK operators primarily employ malvertising to ensure a high infection rate and large-scale coverage.
As a result, visitors using a vulnerable version of a browser to access an actor-controlled web page or a compromised-but-legitimate website are redirected using malicious JavaScript code to a proxy server, which, in turn, communicates with an exploit server to deliver the appropriate browser exploit.
The exploit server, for its part, detects the user’s browser by parsing the User-Agent string and returns the exploit that “matches the pre-defined vulnerable browser versions.”
“The artful design of the Exploit Kit allows it to infect devices with little to no interaction from the end user,” the researchers said. “Meanwhile, its use of proxy servers makes infections harder to detect.”
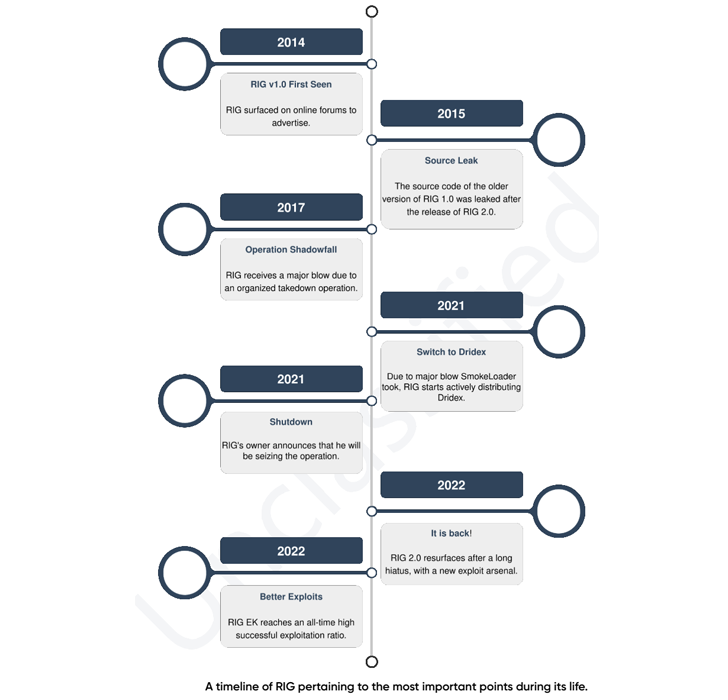
Since arriving on the scene in 2014, RIG EK has been observed delivering a wide range of financial trojans, stealers, and ransomware such as AZORult, CryptoBit, Dridex, Raccoon Stealer, and WastedLoader. The operation was dealt a huge blow in 2017 following a coordinated action that dismantled its infrastructure.
Recent RIG EK campaigns have targeted a memory corruption vulnerability impacting Internet Explorer (CVE-2021-26411, CVSS score: 8.8) to deploy RedLine Stealer.