North Korean Affiliates Suspected in $40M Cryptocurrency Heist, FBI Warns
The U.S. Federal Bureau of Investigation (FBI) on Tuesday warned that threat actors affiliated with North Korea may attempt to cash out stolen cryptocurrency worth more than $40 million.
The law enforcement agency attributed the blockchain activity to an adversary the U.S. government tracks as TraderTraitor, which is also known by the name Jade Sleet.
An investigation undertaken by the FBI found that the group moved approximately 1,580 bitcoin from several cryptocurrency heists over the past 24 hours and are currently said to be holding those funds in six different wallets.
North Korea is known to blur the lines among cyber warfare, espionage, and financial crime. TraderTraitor, in particular, has been linked to a series of attacks targeting blockchain and cryptocurrency exchanges with the goal of plundering digital assets to generate illicit revenue for the sanctions-hit nation.

This includes the $60 million theft of virtual currency from Alphapo on June 22, 2023; the $37 million theft of virtual currency from CoinsPaid on June 22, 2023; and the $100 million theft of virtual currency from Atomic Wallet on June 2, 2023, as well as attacks targeting Sky Mavis’ Ronin Network and Harmony Horizon Bridge last year.
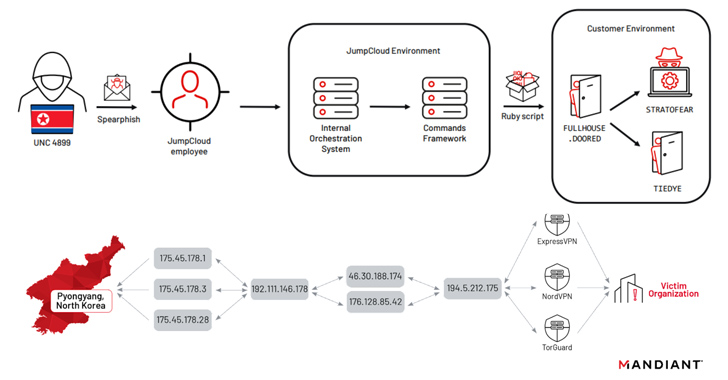
The cluster shares overlap with another North Korean group dubbed APT38 (aka BlueNoroff or Stardust Chollima), which, in turn, is part of the larger Lazarus constellation. Google-owned Mandiant, last month, also connected TraderTraitor to UNC4899, a hacking crew attributed to the JumpCloud hack in late June 2023.
According to data compiled by blockchain intelligence firm TRM Labs, North Korean hackers are estimated to have stolen over $2 billion in cryptocurrencies since 2018 as part of a series of 30 attacks, with $200 million stolen in 2023 alone.
“Private sector entities should examine the blockchain data associated with these addresses and be vigilant in guarding against transactions directly with, or derived from, the addresses,” the FBI said.