Cyberattacks targeting everything from crypto wallets to satellite internet: FortiGuard Labs
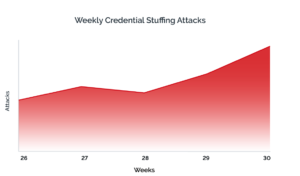
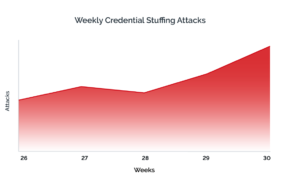
Pre-attack Reconnaissance Increases To Maximize Attacks Like Ransomware Attacks are often discussed in terms of left-hand and right-hand threats when viewed through an attack chain such as the MITRE ATT&CK framework. On the left side of the attack chain are efforts spent pre-attack, which includes planning, development, and weaponization strategies. On the right is the more familiar execution phase of attacks. FortiGuard Labs predicts that cybercriminals will spend more time and effort on reconnaissance and discovering zero-day capabilities to exploit new technologies and ensure more successful attacks. Unfortunately, there will also be an increase in the rate at which new attacks can be launched on the right due to the expanding Crime-as-a-Service market.
Ransomware Will Get More Destructive: There will continue to be a crimeware expansion and ransomware will remain a focus going forward. Ransomware attackers already add to the noise by combining ransomware with distributed denial-of-service (DDoS), hoping to overwhelm IT teams so they cannot take last second actions to mitigate an attack’s damage. Adding a “ticking time bomb” of wiper malware, which could not only wreck data but destroy systems and hardware, creates additional urgency for companies to pay up quickly. Wiper malware has already made a visible comeback, targeting the Olympic Games in Tokyo, for example. Given the level of convergence seen between cybercriminal attack methods and advanced persistent threats (APTs), it is just a matter of time before destructive capabilities like wiper malware are added to ransomware toolkits. This could be a concern for emerging edge environments, critical infrastructure, and supply chains. Cybercriminals Use AI To Master Deep Fakes: Artificial Intelligence (AI) is already used defensively in many ways, such as detecting unusual behavior that may indicate an attack, usually by botnets. Cybercriminals are also leveraging AI to thwart the complicated algorithms used to detect their abnormal activity. Going forward, this will evolve as deep fakes become a growing concern because they leverage AI to mimic human activities and can be used to enhance social engineering…