Threat Spotlight: Stealer Logs & Corporate Access
Executive Overview
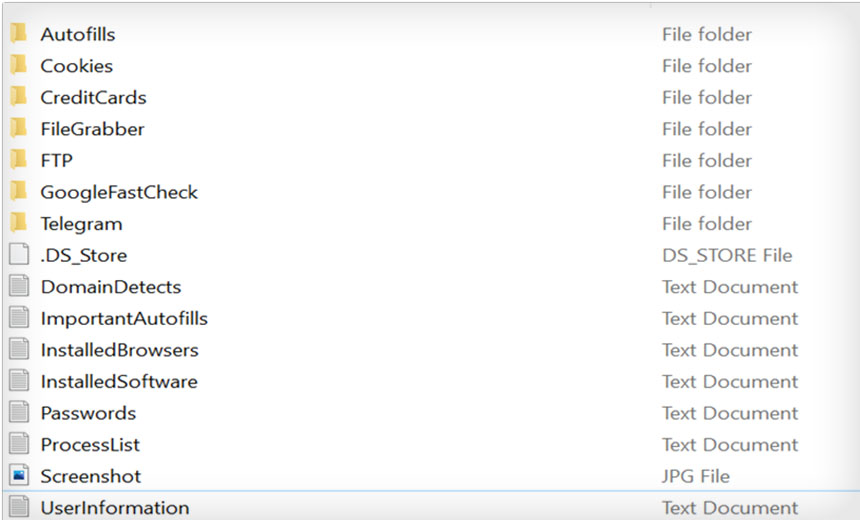
Over the last three years, infostealer malware variants have become a “popular trend” in the cybercriminal Malware-as-a-Service (MaaS) ecosystem. Doing precisely as their category implies, these malware variants steal information from users’ devices. After infecting the device, the malware employs various techniques to remain undetected while sending data to the malicious actors’ command and control infrastructure.
To understand the threat infostealer malware poses, we examined more than 19.6 million stealer logs to identify trends like:
- Number of infections containing corporate credentials
- Average price of infostealers with banking access
- Prominent consumer applications appearing in the logs
Read our full report, Stealer Logs & Corporate Access, or continue reading for the highlights.
The Details
Analyzing more than 19.6 million stealer logs showed trends that indicate malicious actors value access to corporate resources and financial services accounts. Based on the findings, malicious actors appear to use infostealer malware so that they don’t have to purchase a consumer application subscription or so they can steal money by compromising a bank account.
At a high level, the research found the following about stealer logs:
- 376,107 (1.91%): access to corporate SaaS applications
- 48,173: access to a resource that includes a single sign on credential representing almost certain access to corporate resources
- 200,000 (1%): access to leading AI provider credentials
(Note, these are from users of the applications being compromised with infostealer malware. We have no reason to believe that these organizations themselves have suffered a security incident or breach)
Meanwhile, looking at infostealer logs through the eyes of the consumer, the data shows:
- 46.9% had access to Gmail credentials
- $112: average cost of financial services-related logs compared to $15 across all log sales
We collected data from four primary sources:
- Public Telegram “logs” channels: “free samples” of primarily consumer application access logs used to advertise the paid Telegram rooms
- Private Telegram channels: invitation-only, paid channels with higher-value logs
…