Russian influence and cyber operations adapt for long haul and exploit war fatigue
Since July 2023, Russia-aligned influence actors have tricked celebrities into providing video messages that were then used in pro-Russian propaganda. These videos were then manipulated to falsely paint Ukrainian President Volodymyr Zelensky as a drug addict. This is one of the insights in the latest biannual report on Russian digital threats from the Microsoft Threat Analysis Center: “Russian Threat Actors Dig In, Prepare to Seize on War Fatigue”
As described in more detail in the report, this campaign aligns with the Russian government’s broader strategic efforts during the period from March to October 2023, across cyber and influence operations (IO), to stall Ukrainian military advances and diminish support for Kyiv.
Video messages from American celebrities are used in Russian propaganda
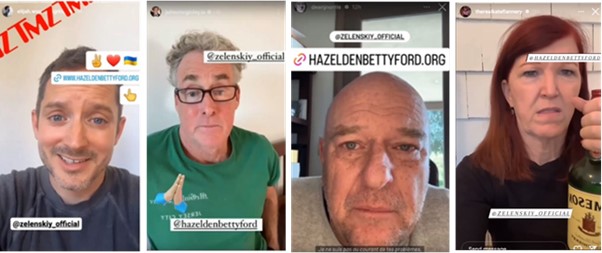
Unwitting American actors and others appear to have been asked, likely via video message platforms such as Cameo, to send a message to someone called “Vladimir”, pleading with him to seek help for substance abuse. The videos were then modified to include emojis, links and sometimes the logos of media outlets and circulated through social media channels to advance longstanding false Russian claims that the Ukrainian leader struggles with substance abuse. The Microsoft Threat Analysis Center has observed seven such videos since late July 2023, featuring personalities such as Priscilla Presley, musician Shavo Odadjian and actors Elijah Wood, Dean Norris, Kate Flannery, and John McGinley.
Samples of the videos promoting pro-Russian propaganda aiming to malign Ukrainian President Volodymyr Zelensky that feature different celebrities
Prigozhin’s death has not slowed Russia’s influence operations
The August 2023 death of Russian businessman Yevgeny Prigozhin, who owned the Wagner Group and the infamous Internet Research Agency troll farm, led many to question the future of Russia’s influence and propaganda capabilities. However, since then, Microsoft has observed widespread influence operations by Russian actors that are not linked to Prigozhin, indicating that Russia has the capacity to continue prolific and sophisticated malign influence operations without him.