Credential Theft, O365 Lures Dominate Corporate Inboxes in Q1

phishing attacks that targeted corporate users. In this post, we break down these attacks and shed light on the phishing emails that are making it into corporate inboxes.
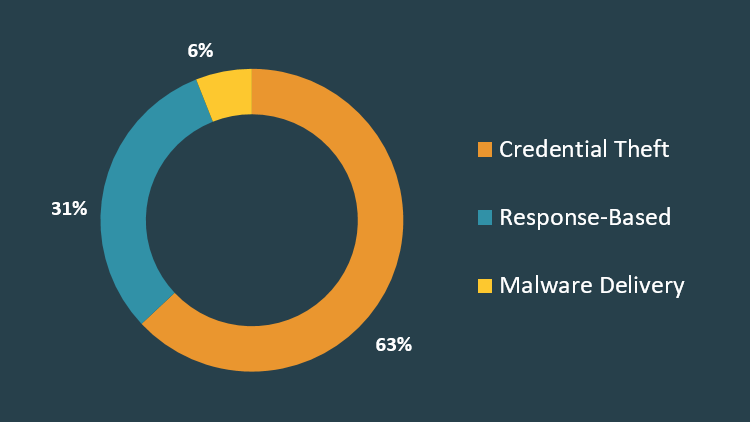
Threats Found in Corporate Inboxes
Credential Theft
Credential theft attacks continue to be the most prolific threats observed in corporate inboxes. In Q1, nearly two-thirds of all reported email threats attempted to steal credentials. This was an 11.6% increase from Q4 2020.
Eighty-four percent of credential theft phishing attacks contained a link that led to a web page with a login form designed to harvest credentials. The remaining 16% delivered attachments similarly designed to lead victims to fake sites and steal sensitive information. Both tactics rely heavily on brand impersonation.
O365
Microsoft Office 365 continued to be targeted heavily in Q1. More than 44% of credential theft email lures targeted O365 logins. This is a 10.4% increase from Q4 2020.
Response-Based
Response-based attacks such as BEC and 419 scams continued to thrive during Q1, contributing to 31% of total phishing emails that targeted corporate users. Advanced-Fee or 419 scams contributed to 60.6% of reported response-based threats.
Breakdown of response-based threats:
- 419 (60.6%)
- BEC (19.7%)
- Job Scams (7.7%)
- Vishing (6.3%)
- Tech Support (5.7%)
$1.8 Billion.
Malware
In Q1, 6% of reported phishing lures delivered attachments or links to malware. This suggests email security controls are far better at detecting malicious code in email traffic than they are at detecting social engineering techniques.
one-day spike in attacks in February that represented one of the largest surges of a single payload we have seen in a 24-hour period.
ZLoader and…
