Joker Android Malware Dupes Its Way Back Onto Google Play
A new variant of the Joker malware has hoodwinked its way onto the Google Play marketplace yet again, in 11 Android apps that were recently removed.
Mobile Security – Threatpost
A new variant of the Joker malware has hoodwinked its way onto the Google Play marketplace yet again, in 11 Android apps that were recently removed.
Mobile Security – Threatpost
Android malware once found a way onto phones before they even shipped The Verge
Google has detailed a method by which malware was able to get on Android phones virtually at the factory, before customers have even opened the box, much …

A staggering 590 million resumes have leaked from poorly-secured Chinese companies in just the last three months.
Read more in my article on the Tripwire State of Security blog.
Enlarge (credit: Christiaan Colen / Flickr)
Malware pushers are experimenting with a novel way to infect Mac users that runs executable files that normally execute only on Windows computers.
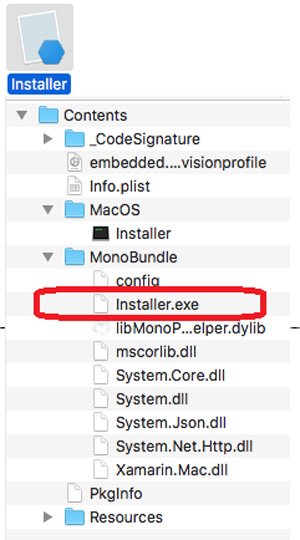
The files and folders found inside a DMG file that promised to install Little Snitch. (credit: Trend Micro)
Researchers from antivirus provider Trend Micro made that discovery after analyzing an app available on a Torrent site that promised to install Little Snitch, a firewall application for macOS. Stashed inside the DMG file was an EXE file that delivered a hidden payload. The researchers suspect the routine is designed to bypass Gatekeeper, a security feature built into macOS that requires apps to be code-signed before they can be installed. EXE files don’t undergo this verification, because Gatekeeper only inspects native macOS files.
“We suspect that this specific malware can be used as an evasion technique for other attack or infection attempts to bypass some built-in safeguards such as digital certification checks, since it is an unsupported binary executable in Mac systems by design,” Trend Micro researchers Don Ladores and Luis Magisa wrote. “We think that the cybercriminals are still studying the development and opportunities from this malware bundled in apps and available in torrent sites, and therefore we will continue investigating how cybercriminals can use this information and routine.”
Read 5 remaining paragraphs | Comments