Chrome Supports Key Pinning on Android to Improve Security
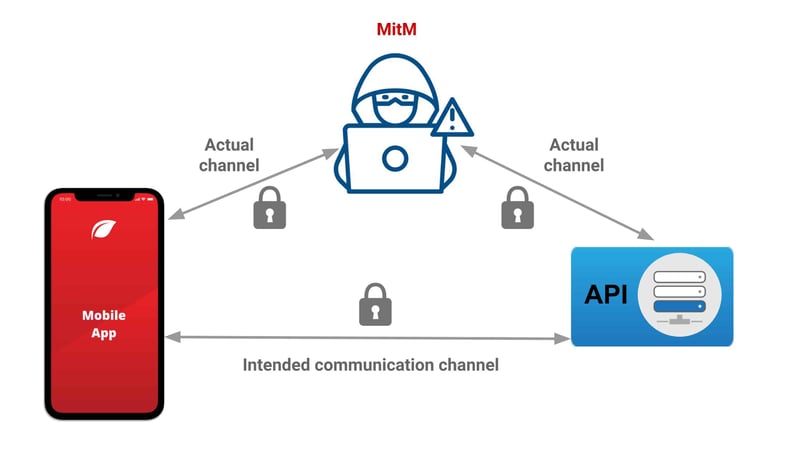
Key pinning, a technique used to prevent an attacker from tricking a vulnerable certificate authority (CA) into issuing an apparently valid certificate for a server, is now used in Chrome for Android, version 106. This helps preventing man-in-the-middle attacks against Google services.
As Chrome security engineers David Adrian, Joe DeBlasio, and Carlos Joan Rafael Ibarra Lopez explain, key pinning was devised at Google as a response to real attacks seen in the wild, specifically an attack that targeted Google services in 2011.
Key pinning was born as an extension to the HTTP protocol, later deprecated, that enabled sending an HTTP header that tells user agents to “pin” cryptographic identities over a period of time.
During that time, user agents (UAs) will require that the host presents a certificate chain including at least one Subject Public Key Info structure whose fingerprint matches one of the pinned fingerprints for that host.
This effectively reduces the number of CAs that can authenticate the domain while the identity is pinned. While effective, key pinning has its own drawbacks. For example, if pins get out of date, there’s a risk of locking users out of a service, which leads to a number of good practices:
Whenever pinning, it’s important to have safety-valves such as not enforcing pinning (i.e. failing open) when the pins haven’t been updated recently, including a “backup” key pin, and having fallback mechanisms for bootstrapping.
These mechanisms are hard for individual sites to manage, say Google engineers, which, as mentioned, led to the RFC being deprecated. As a matter of fact, Google removed public key pinning from Chrome in 2017. But key pinning may still have its own use cases, including web browsers, automatic software updates, and package managers, where client and server are operated by the same entity.
Specifically, in Google’s case, thanks to the control that the company has on its browser, Chrome embeds pinned certificates (pins) for all Google properties. This means every HTTPS access is only authenticated through a key belonging to the embedded set of pins.
To fully understand what role key pinning plays into Chrome…