What Is Microsoft’s Pluton Security Processor and Why You Need It
Microsoft has been ramping up the security of its ecosystem one step at a time. Windows 11 set the tone by making the TPM 2.0 chip mandatory for upgrade and installation. Taking it to the next level, the PC giant has introduced the Pluton Security Processor. So what is PSP or Pluton Security Processor, do you need it, and how or where can you get it? Let’s find out.
What Is a Pluton Security Processor?
Microsoft has partnered with popular chip makers like Intel, AMD, and Qualcomm to develop a new security chip named Pluton Security Processor. It has been designed as a hardware unit that will be directly planted in the CPUs of upcoming computers. Why?
The chip provides tighter integration between the hardware (motherboard) and software (Windows OS and apps). Pluton aims to make it harder for hackers to break into computers and steal data or seize system access, even with physical access to the computer.
But don’t we have TPM chips for that?
Differences Between TPM and PSP
TPM or Trusted Processor Modules are hardware components that resides in your computer but are separate from the motherboard. While they do encrypt data and protect the user from several kinds of attacks, they fail to offer protection from an entire spectrum or vector of advanced attacks. For example, when the hacker has physical access to the computer, TPM chips can do little to protect the data’s integrity.
Another issue is that because TPM is not part of the motherboard, it needs a channel of communication to transfer data back and forth. This leaves the channel open for hackers to intercept and manipulate.
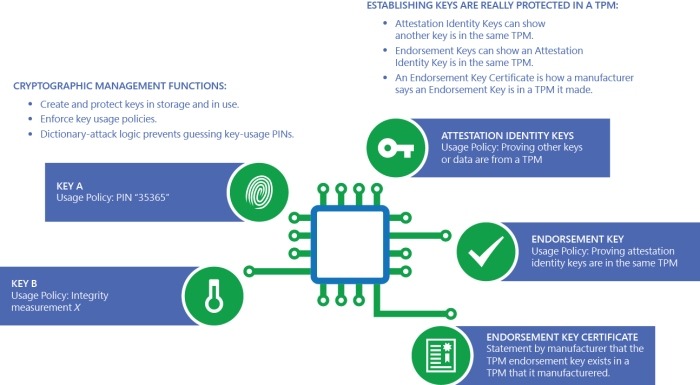
TPM chips, though supported by Windows and powering security solutions like Windows BitLocker and Hello, are not default on most computers. With Pluton Security Processors, Microsoft wants to address these issues by partnering with big-name manufacturers and making Pluton the default standard.
Because the security chip is part of the motherboard and tightly integrated, there is no need to depend on an…