Facebook account hacked? How this Aussie dad recovered his profile after distraction scam
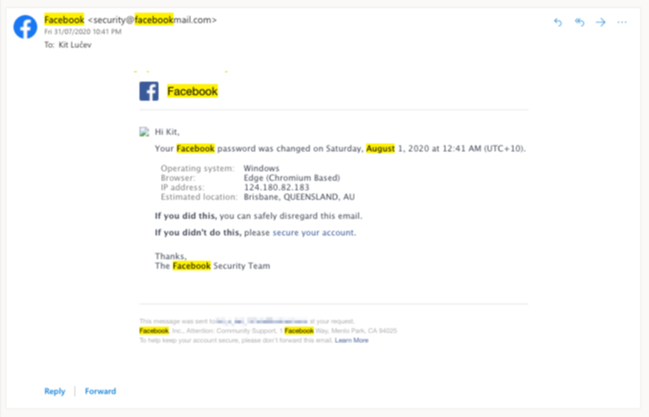
Kit Lucev woke up on August 1, 2020, to a strange email.
His Facebook account had been suspended.
“I assumed it was some sort of error, so I logged on, expecting that I’d get my account reinstated,” he told 7NEWS.com.au.
But it wasn’t that simple.
The 31-year-old had fallen victim to an increasingly popular distraction technique where hackers target accounts linked to a business page that has likely purchased Facebook advertising in the past using a saved payment method.

Once the account is compromised, the hacker changes the password and shares photographs they know will trigger Facebook’s community standards – such as terrorist group imagery or child pornography.
While the victim is busy attempting to regain control of their account, the hackers use their payment details to purchase Facebook ads for their own pages – often based overseas.
It all became clear for Kit when he received a message from a friend, a fly-in-fly-out worker who is “up at all hours of the night”.
“What’s with all that ISIS stuff that you were posting last night? That’s not funny,” the message read.
Kit’s personal account had been linked to a business page – a page for his side business selling footy merchandise and one he had spent thousands of dollars on in Facebook ads.
Thankfully, the hacker had tried but failed to use his credit card to buy $408 in advertisements. Despite several attempts, the purchase was unable to be processed and to Kit’s knowledge, they didn’t spend a single cent.
But his problems were far from over.

Kit appealed the suspension and Facebook said it would investigate but warned it may take time.
“I was a bit annoyed, thinking it would take two days. Then two days turned into a week, then a month, then six months,” he said.
During this time, Kit’s side business Uncle Bushchook had gone from making more than $100,000 at its peak in 2017/18 to less than $5000 last year without Facebook, and any way to connect with his 20,000 loyal followers.
“It absolutely was impacted….


