CheckMate ransomware targets popular file-sharing protocol
The CheckMate ransomware operators have been targeting the Server Message Block (SMB) communication protocol used for file sharing to compromise their victims’ networks.
Unlike most ransom campaigns, CheckMate, discovered in 2022, has been quiet throughout its operations. To the best of our knowledge, it doesn’t operate a data leak site.
That’s quite unusual for a ransomware campaign since many prominent gangs brag about big targets and post them as victims on their data leak sites. They do this to raise the pressure for a victim to pay the ransom.
Cybernews research has recently detected new CheckMate activity. It turns out the gang has been actively targeting weakly-protected SMB shares.
After gaining access to SMB shares, threat actors encrypt all files and leave a ransom note demanding payment in exchange for the decryption key.
Gang linked to Russia
The ransomware gang is known to be operating Kupidon, Mars, and CheckMate ransomware. All three types of malicious programs were discovered in 2021-22 and are believed to be of Russian origin.
According to Cybernews researchers, the impact of ransomware can be significant and wide-ranging. Risks to victims include:
- Financial loss
- Data loss
- Disruption of business operations
- Reputation damage
- Spread of malware
- Legal and regulatory consequences
While we don’t have enough information on the average ransom amount the gang demands from its victims, some publicly shared ransom notes indicate the group might be relatively modest. Typical amounts demanded are around $15,000 for the decryptor.
That’s a relatively small demand by usual standards. According to the recent report by the cybersecurity firm Coveware, average ransom payments during the last quarter of 2022 were over $400,000.
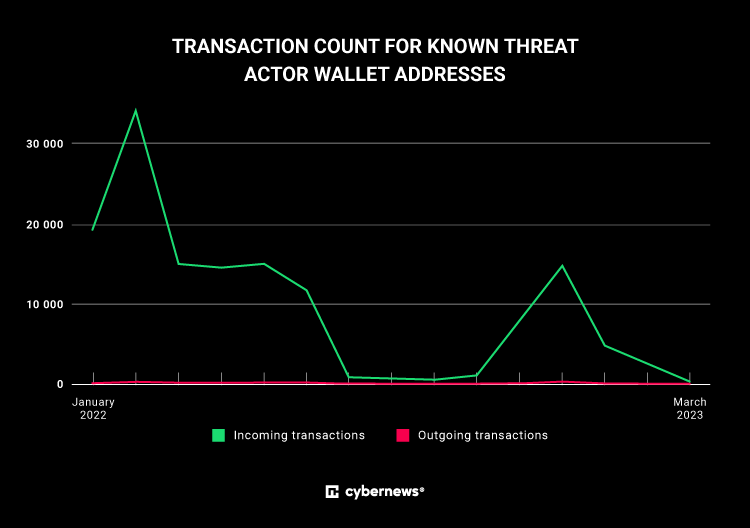
The Cybernews investigation identified crypto wallet addresses associated with the CheckMate operators and found thousands of incoming transactions in the first quarter of 2023. However, we can’t say with certainty that those transactions came from CheckMate’s victims.
Last year, QNAP, a network-attached storage (NAS) vendor, warned customers about the CheckMate ransomware activity going after internet-exposed SMB…