Malware found preinstalled In push-button phones sold In Russia

Credit: ValdikSS
Malicious code was identified in the firmware of four low-cost push-button phones sold through Russian internet stores, according to a security researcher.
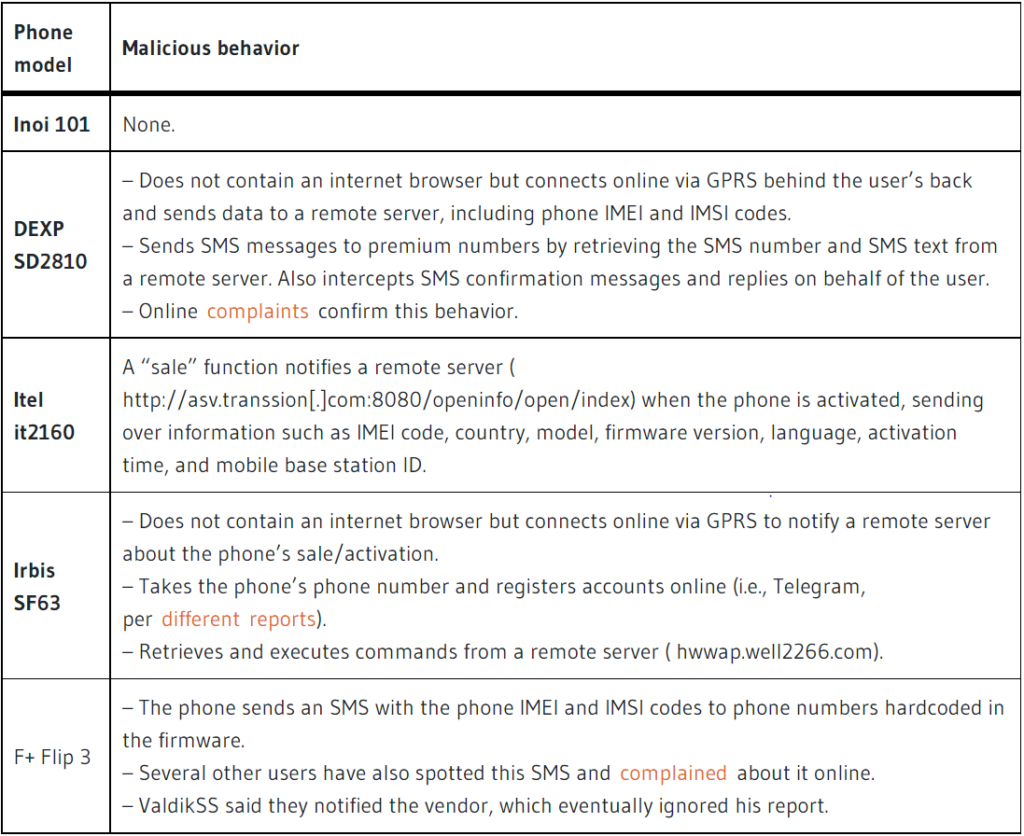
Push-button phones such the DEXP SD2810, Itel it2160, Irbis SF63, and F+ Flip 3 were captured subscribing users to premium SMS services and intercepting incoming SMS messages to avoid detection, according to a report published this week by a Russian security researcher named ValdikSS.
Even if the phones didn’t have an internet browser, the devices discreetly notified a remote internet server when they were activated for the first time, according to ValdikSS, who set up a local 2G base station to intercept the phones’ connections.
ValdikSS says he put five ancient phones he acquired online to the test. A fifth phone, the Inoi 101, was also put to the test, but none of the devices were found to be malicious.
Credit : therecord.media
All of the distant servers that received this activity, according to ValdikSS, were located in China, where all of the devices were also made before being re-sold on Russian internet retailers as low-cost substitutes to more popular push-button phone options, such as Nokia’s.
Although the malicious code was discovered in the phone’s firmware, the researcher couldn’t say if it was installed by the manufacturer or by third parties that supplied the firmware or handled the phones during distribution.
Backdoors, mobile phone supply chains, and malware
While audacious, such events are no longer uncommon, and identical cases have been identified on multiple occasions in the last five years.
- November 2016 – According to reports from Kryptowire and Anubis Networks, two Chinese businesses that made firmware components for major Chinese phone manufacturers discreetly embedded a backdoor-like functionality in their code.
- December 2016– Dr.Web discovered malware in the firmware of 26 different Android smartphone models.
- July 2017 – Dr.Web discovered Triada banking trojan versions buried in the firmware of a number of Android cellphones.
- March 2018 – The identical Triada malware was discovered in the firmware of 42 different Android smartphone models by Dr.Web.
- May 2018 –…



