Making Sense of RFCs: Reading List
If you’re looking for resources to help you learn about the world of cybersecurity, here are the 7 RFCs Roxy, Hurricane Labs’ Director of Compliance, recommends you start with. Looking for more details? Check out their webinar, Making Sense of RFCs!
The List
1. RFC 2196 Site Security Handbook
RFC 2196 (Site Security Handbook) “is a guide to developing computer security policies and procedures for sites that have systems on the Internet.” It goes over, in detail, such topics as why you’d want a security policy and how to handle incident response.
2. RFC 2504 Users’ Security Handbook
Even though it was written in 1999, RFC 2504 (Users’ Security Handbook) has advice that still hasn’t aged much, such as “How to Prepare for the Worst in Advance” and “Encrypt Everything… Shred Everything Else.”
3. RFC 6274 Security Assessment of [IPv4]
Written in 2011, RFC 6274 (Security Assessment of IPv4) uses several RFCs as sources and fully describes IPv4 and considers the security of its features. It includes known issues that have not previously been addressed by other RFCs.
4. RFC 6454 The Web Origin Concept
RFC 6454 mentions security implications of the same-origin policy. Web Origin is, according to Mozilla, “defined by the scheme (protocol), hostname (domain), and port of the URL used to access it. Two objects have the same origin only when the scheme, hostname, and port all match.”
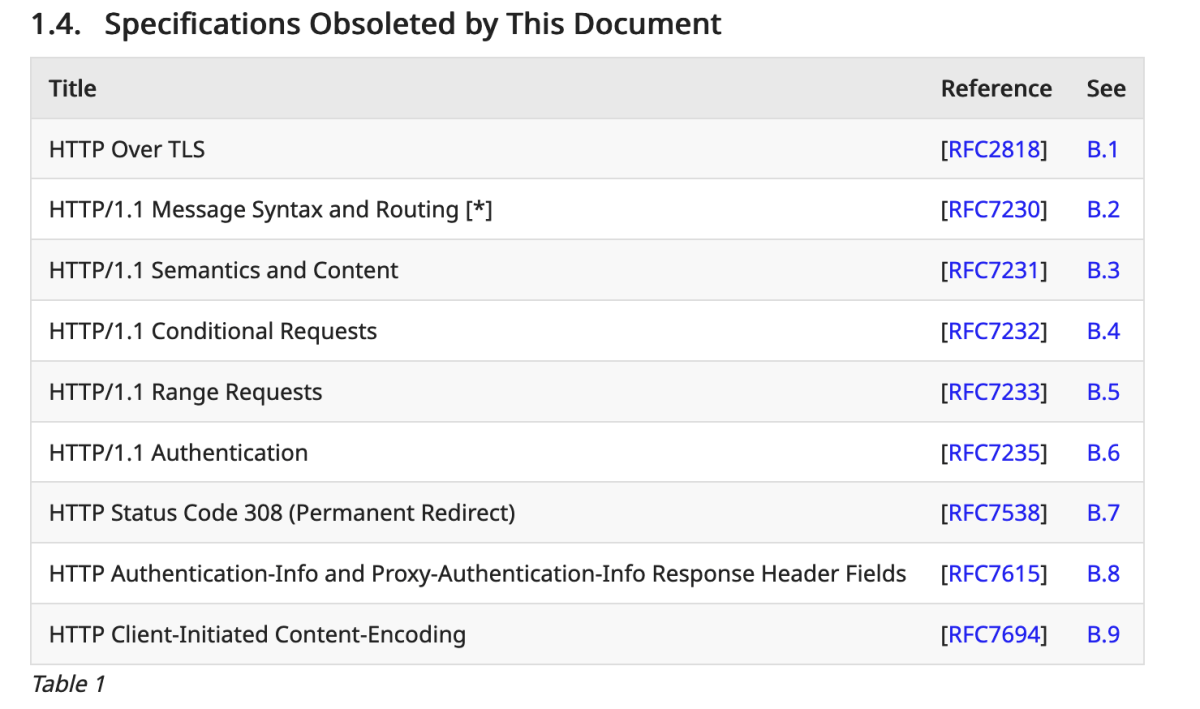
5. RFCs 9110 HTTP Semantics
Just released this week, RFC 9110 (HTTP Semantics) obsoletes most of the HTTP RFCs mentioned in our webinar. It explains the “Core Semantics” of HTTP, regardless of version, which are important to understand when observing and working with HTTP traffic. There are also new RFCs for HTTP 1.1 (9112), HTTP 2 (9113), and HTTP 3 (9114).
Table 1 from RFC 9110 shows all the RFCs it obsoletes: