Google’s Project Zero revises vulnerability disclosure timelines to increase patch adoption
NEW DELHI: Google’s cybersecurity division, Project Zero, has changed its disclosure policies today with the intent to “refocus on reducing the time it takes for vulnerabilities to get fixed”, in the industry right now. The Project Zero team, which deals with vulnerabilities in hardware and software systems, will report vulnerabilities earlier if a company hasn’t fixed the flaw in record time.
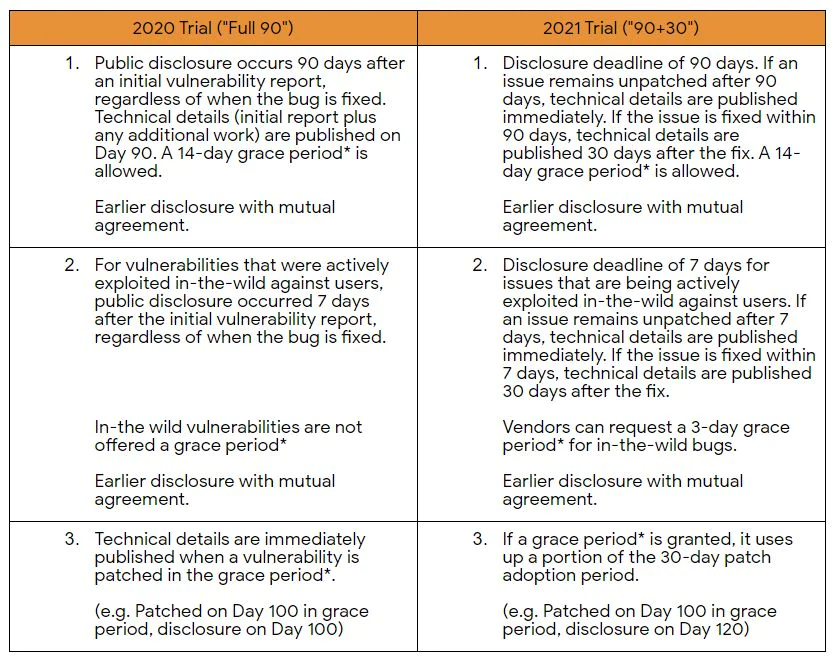
“Project Zero won’t share technical details of a vulnerability for 30 days if a vendor patches it before the 90-day or 7-day deadline. The 30-day period is intended for user patch adoption,” the company said in a blog post.
The team used to provide a 90-day period after issuing a vulnerability report, followed by a 14-day grace period, before it published details of the vulnerability. Now, if an issue remains unpatched after the 90 days, Google will publish the details immediately. This is likely aimed at making users download patches quickly, once a company issues them.
Further, for vulnerabilities that are being actively exploited by hackers, Google will publish details immediately if the said issues remain unpatched after 7 days of reporting them. If the issue is fixed within the 7 days, then Google will wait 30 days before publishing the vulnerabilities. The company used to offer no grace period on such reports but will allow hardware and software vendors to request for an additional three-day grace period now.
The Project Zero team said the changes are aimed at shortening the time elapsed between a bug report and its patch being made available to users. It also wants to ensure “thorough patch development” and “improved patch adoption” once a patch is released by the affected vendor.
Google’s decision comes on the heels of a general increase in cybersecurity issues around the world last year. According to a March report from the Indian Computer Emergency Response Team (CERT-In), cyber security incidents in India grew from 3,94,499 in 2019 to 11,58,208 in 2020, which is a nearly 200% increase.