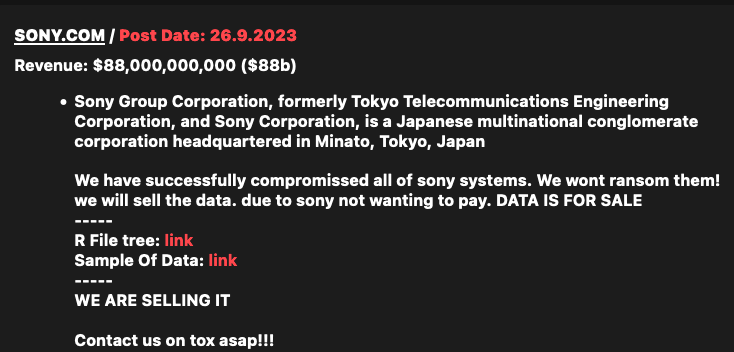
Roku Suffers Data Breach, Hackers Sell Credentials of Hundreds of 15,000 Stolen Accounts
Streaming platform Roku officially discloses hackers have successfully breached its systems to steal more than 15,000 customer accounts containing sensitive information. Hundreds of the accounts are reportedly being sold online as the breach has given hackers access to the owner’s stored credit card information to make illegal purchases.
With over 80 million active users, the firm reportedly disclosed the hack on Friday in documents it filed with the attorneys general of Maine and California. Fifteen thousand three hundred sixty-three accounts were compromised between December 28, 2023, and February 21, 2024, according to the papers.
The documents show that hackers gained access to the accounts by obtaining login credentials from other sources, instead of getting into Roku’s system. Using a hacking technique called a credential stuffing assault, threat actors gather credentials that have been made public in past data breaches and then try to use them to access other websites.

(Photo : THOMAS SAMSON/AFP via Getty Images)
An agent of the operational center of the French National Cybersecurity Agency (ANSSI) checks datas on a computer in Paris on November 24, 2022.
According to the firm, once an account was compromised, threat actors were able to alter all of the user’s data, including passwords, email addresses, and shipping addresses.
Roku clarified, however, that the unauthorized actors who gained access to the impacted Roku accounts did not have dates of birth, social security numbers, complete payment account numbers, or any other kind of sensitive personal information that needed to be disclosed.
This essentially locked the user out of the account, enabling threat actors to utilize the saved credit card information to make transactions without sending order confirmation emails to the actual account holder.
According to BleepingComputer, several threat actors are employing the Open Bullet 2 or SilverBullet cracking tools to carry out credential-stuffing assaults. With the help of these apps, hackers can import custom configuration files made specifically to carry out credential-stuffing attacks against particular…