Tag Archive for: setup
Pixel 6 Pro setup screen accidentally reveals face unlock option for one user
/in Mobile Security
What you need to know
- New evidence of face unlock support for the Pixel 6 Pro has surfaced.
- The unreleased biometric feature inadvertently appeared as a backup security option when a user was setting up their new Pixel 6 Pro.
- However, it remains inoperable on Google’s latest flagship phone.
Face unlock support for the Pixel 6 Pro has been rumored since late last year, but Google has yet to enable the security method despite having released two Feature Drops. Now, a new piece of evidence suggests the search giant is preparing to launch it in a future update.
According to a Reddit user who recently purchased a new Pixel 6 Pro, the face unlock option showed up during the phone’s initial setup as one of the backup screen lock methods. It specifically appeared alongside the PIN, pattern, password, and fingerprint options on the “Choose a screen lock” page.
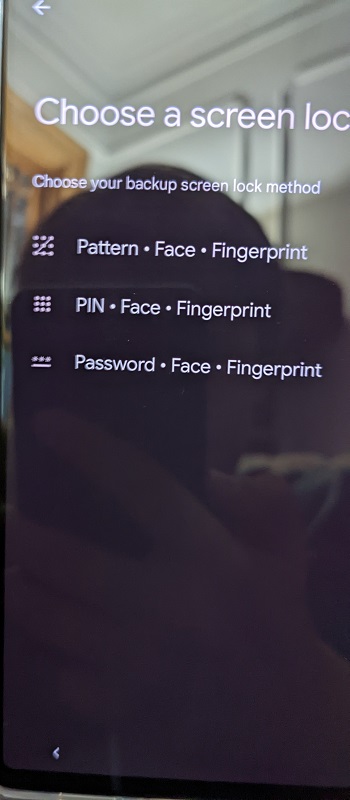
Unfortunately, the feature is not functional because the user found no option to turn it on during the phone’s configuration. Face unlock was nowhere to be found in the settings menu either. It’s anybody’s guess why it appeared on the setup page right now.
According to 9to5Google, the face unlock reference has been tucked away inside the Pixel 6 Pro’s Android 12 builds since as early as October 2021. These findings seem to back up earlier speculation that Google ditched the feature at the last minute before unveiling the Pixel 6 series. Face unlock was rumored to be a feature of Google’s best Android phones prior to their launch, but they only arrived with an in-display fingerprint sensor.
Most recently, traces of the feature were spotted in Google’s Android 12 QPR3 Beta 1.1 interim update.
What’s curious about its latest sighting is that it showed up on the stable channel. While the feature’s appearance on the Pixel 6 Pro might have been a fluke, Pixel fans may now have another reason to hope for its future arrival.
That said, Google has consistently kept the release date of face unlock a closely guarded secret, and only time will tell whether it will be included in a future software update.
Hackers Setup Fake Cyber Security Firm To Target Security Researchers
/in Internet Security
Google’s Threat Analysis Group (TAG), a Google security team specialized in hunting advanced persistent threat (APT) groups, on Wednesday shared that a North Korean government-backed campaign is targeting cybersecurity researchers with malware via social media.
For those unaware, in January 2021, TAG had disclosed a hacking campaign, targeting security researchers working on vulnerability research and development across different organizations. On March 17th, the same actors behind those attacks set up a new website for a fake company called “SecuriElite” as well as associated Twitter and LinkedIn accounts.
The new website claims that it is an “offensive security company located in Turkey that offers pentests, software security assessments and exploits”.
As per the experts, this website has a link to their PGP public key at the bottom of the page like the previous websites set up by the actor. The PGP key hosted on the attacker’s blog acted as the lure for unsuspecting researchers in January attacks to visit the site “where a browser exploit was waiting to be triggered”.
The attacker’s latest batch of social media profiles continues the trend of posing as fellow security researchers interested in exploitation and offensive security. In total, Google has identified eight Twitter accounts and seven LinkedIn profiles.
The threat actors used multiple platforms to communicate with potential targets, including Twitter, LinkedIn, Telegram, Discord, Keybase and email to communicate with the researchers and build trust, only to deploy a Windows backdoor through a trojanized Visual Studio Project.
Following the discovery, Google reported all identified social media profiles to the platforms to allow them to take appropriate action, after which all of them were suspended.
The accounts seemed to be owned by vulnerability researchers and human resources personnel at various security firms including Trend Macro (a fake name inspired by Trend Micro), while some posed as the Chief Executive Officer and employees at the fictitious Turkish company.
Currently, the new attacker website is not serving any malicious content to deliver malware; however, Google has added the…




