Meet LINK: The Easy Way To Handle All Your Document Workflows On Your Mobile Device In A Single App

When was the last time you went to work (or anywhere, really) without some kind of mobile device with you? Since the adoption of mobile devices, the answer is probably never. When was the last time you felt you could adequately handle all your work on that mobile device? If you’re like most lawyers, the answer is, again, probably never.
The legal profession today is a mobile one, with attorneys practicing anywhere and everywhere with the help of smartphones and tablets. As ubiquitous as they are, though, most lawyers would say they can’t handle all the meaningful work they need to handle on those devices, due to poor document workflows, security concerns, and usability.
What if I told you that you really could handle all your work in one app on your mobile device? It might sound too good to be true, but it’s possible with the LINK app from Mobile Helix.
LINK is finally making it possible to handle documents in a meaningful way on all your devices. LINK combines convenient workflows, document management, search, review, annotation, comparison, editing capabilities, and email management in one app that you can actually use from your phone or tablet.
Do Everything, Everywhere With LINK
When you think about the tools you use most in your day-to-day work, your document management system (DMS) and Outlook are probably at the top of the list. Working in both on your mobile device, though, has historically been a huge struggle, if not impossible. LINK brings them together in a single, secure, easy-to-use app.
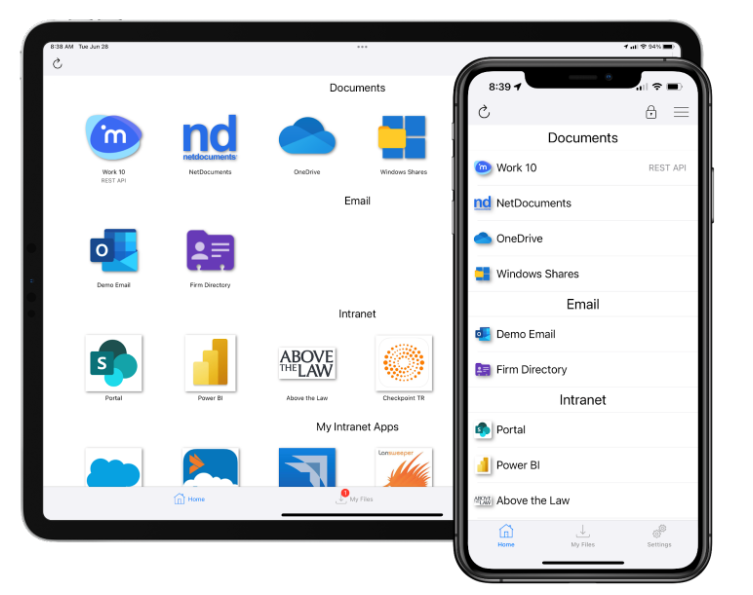
LINK is designed to support the workflows attorneys use all day, every day. The app works with today’s most popular mobile devices – iPhones, iPads, and Android phones and tablets – and supports the three leading document management systems, iManage Work®, NetDocuments, and eDocs by OpenText.
LINK is solving the pervasive problem of lawyers being unable to adequately work on their mobile devices. With LINK, lawyers can fully access their documents, compare them, mark them up, edit them, email them, and more, as easily and securely as they can on a computer.
LINK’s Top Features for Simpler Workflows
Lawyers have long asked for a way to be able to work with their…