Hackers Exploit Bug In Magento To Access Payment Data On Ecommerce Sites
(MENAFN– Investor Brand Network) A critical flaw in the open-source e-commerce platform Magento has allowed hackers to make backdoors into e-commerce websites and
steal payment data . Computer software company Adobe Inc. describes the error,
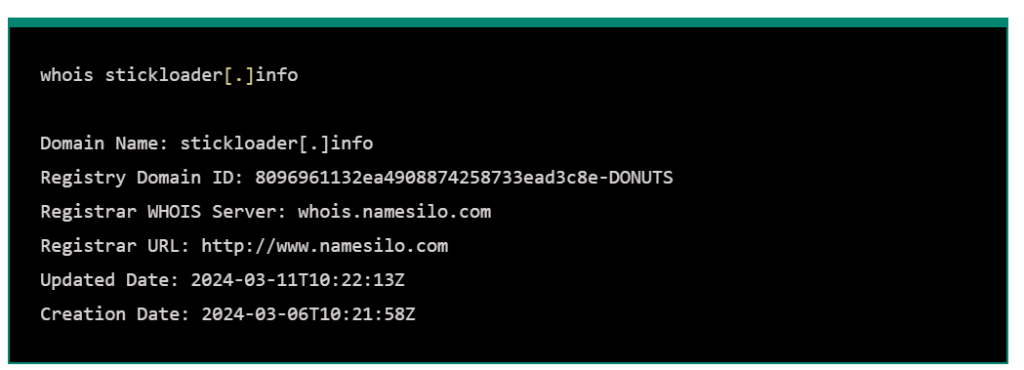
CVE-2024-2072 ,
as the“improper neutralization of special elements” that could allow attackers to make arbitrary code executions without any user interaction.
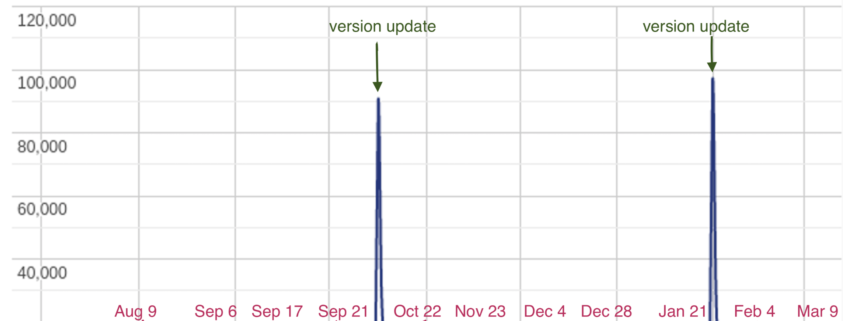
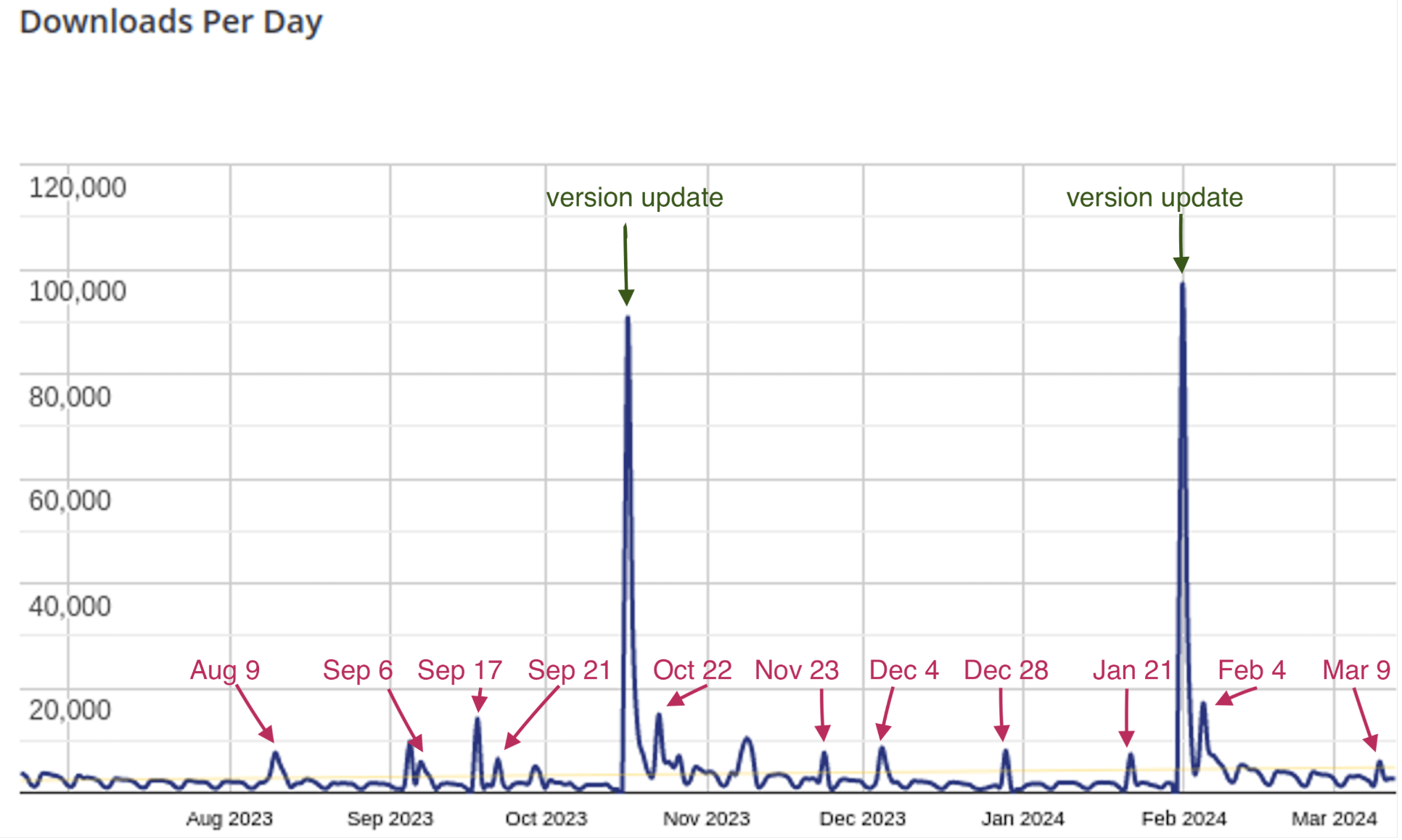
Adobe addressed the vulnerability on Feb. 13, 2024, as part of a batch of security updates while e-commerce security company Sansec announced that it…
Read More>>
NOTE TO INVESTORS:
The latest news and updates relating to NextPlat Corp. (NASDAQ: NXPL, NXPLW) are available in the company’s newsroom at
About BioMedWire
BioMedWire
(“BMW”) is a specialized communications platform with a focus on the latest developments in the Biotechnology (BioTech), Biomedical Sciences (BioMed) and Life Sciences sectors. It is one of 60+ brands within the
Dynamic Brand Portfolio
@
IBN
that delivers :
(1) access to a vast network of wire solutions via
InvestorWire
to efficiently and effectively reach a myriad of target markets, demographics and diverse industries ;
(2) article and
editorial syndication to 5,000+ outlets ;
(3) enhanced
press release enhancement
to ensure maximum impact ;
(4)
social media distribution
via IBN to millions of social media followers ;
and (5) a full array of tailored
corporate communications solutions . With broad reach and a seasoned team of contributing journalists and writers, BMW is uniquely positioned to best serve private and public companies that want to reach a wide audience of investors, influencers, consumers, journalists and the general public. By cutting through the overload of information in today’s market, BMW brings its clients unparalleled recognition and brand awareness.
BMW is where breaking news, insightful content and actionable information converge.
To receive SMS alerts from BioMedWire,“Biotech” to 888-902-4192 (U.S. Mobile Phones Only)
For more information, please visit
Please see full terms of use and disclaimers on the BioMedWire website applicable to all content provided by BMW, wherever…