In Worrisome Development, ‘Skimmers’ Hack Gas Pumps to Read Credit Cards
A former San Diego Police Officer, Larry Avrech, had gotten a heads up from another former cop about keys being sold on the Internet that could open up gas pumps. Their first question was, is this legal?
Their second question was, why would anyone want to open up a gas pump?
The images Avrech found online showed two “gas pump replacement lock keys.”
The answer comes from Brian Krebs, a former newspaper reporter who is an expert on computers and Internet security.
“For decades, only a handful of master keys were needed to open the vast majority of pumps in America,” Krebs said. “That has changed, but I bet there are some older stations that haven’t yet updated their locks.”
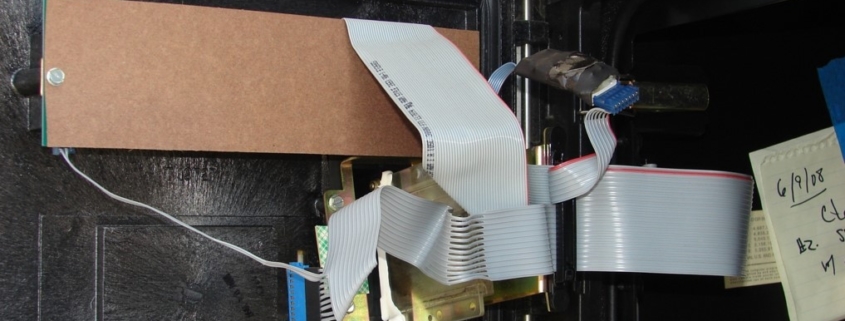
It’s “entirely possible and plausible,” Krebs said, that ”the keys are being used to open pumps. The purpose, he said, is for thieves who use “skimmers.”
Skimmers are a cleverly disguised electronic technology that thieves attach to cash machines, gas pumps and self-service checkout stands to steal credit card data. Krebs, a former Washington Post reporter, explained that the types of skimmers range in sophistication.
In some cases, the thieves must return to the scene of the crime to retrieve the data. More sophisticated strategies use texting to send the data.
In San Diego County, skimmer devices are spot checked as part of 700 inspections of gas stations done annually by San Diego County’s Agriculture Weights and Measures office. Typically, the locations chosen to place skimmers are close to freeways, have easy in-and-out access to a road, do not have a store or kiosk associated with it, and shut down for the night.
Gig Conaughton, communications specialist for the department, said this year inspectors found six skimmers, all of which were removed by the U.S. Secret Service. Conaugton said he couldn’t provide the exact locations “because there is still an ongoing, active investigation.” But he was able to say the inspectors found the skimmers “split at two locations in Santee and National City.”
The Secret Service…