Insight – Horizon3.ai Annual Review Snapshot 2022
As Horizon3.ai wraps up the year with our highly anticipated Horizon3.ai Year in Review (2021-2022): Through the Eyes of the Attacker coming soon, we want to ensure our customers are continuing to think through:
- What does my environment look like?
- Are my security tools effective?
- Did we detect the right activity?
- Are we logging the right things?
- Are my crown jewels and keys to the kingdom– sensitive data and privileged credentials– reachable and exploitable?
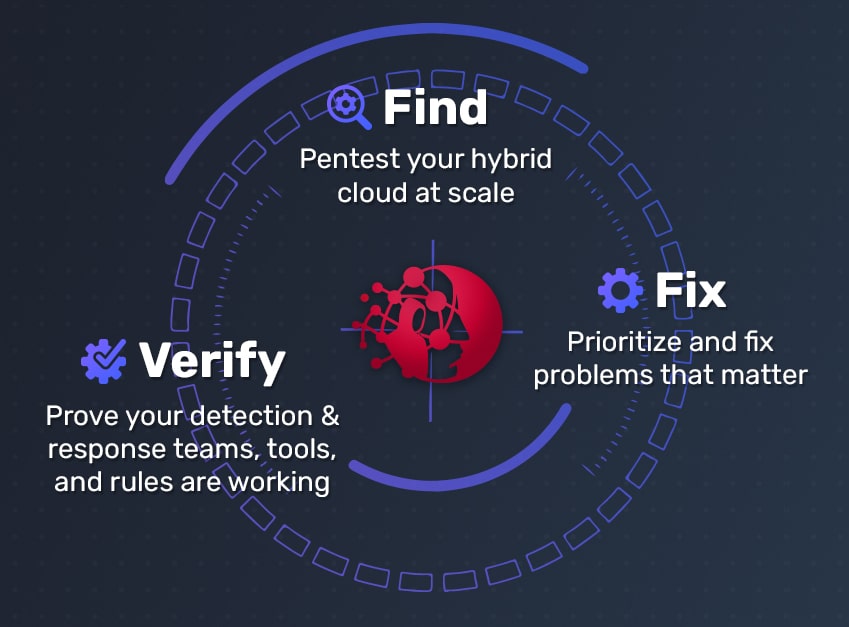 While looking through the eyes of an attacker, Horizon3.ai empowers our customers to gain perspective to answer these questions honestly and accurately, staying relevant to how attackers view their environment. This helps our customers find what is exploitable, fix what matters, and consequentially verify those fix actions.
While looking through the eyes of an attacker, Horizon3.ai empowers our customers to gain perspective to answer these questions honestly and accurately, staying relevant to how attackers view their environment. This helps our customers find what is exploitable, fix what matters, and consequentially verify those fix actions.
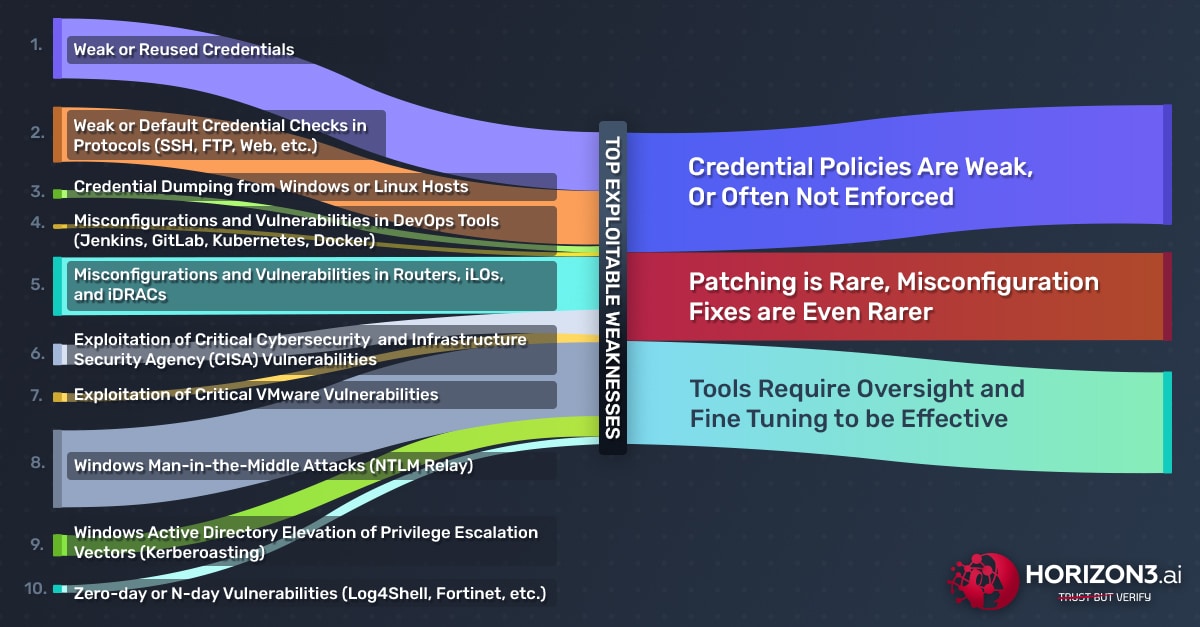
Over the past year, Horizon3.ai pentests revealed cybersecurity vulnerability trends across multiple industry sectors around the globe. Specifically, the top 3 systematic issues NodeZero surfaced are:
- Credential Policies Are Weak, Or Often Not Enforced
- Patching Is Rare, Misconfiguration Fixes Are Even Rarer
- Security Tools Require Oversight and Fine Tuning to be Effective
Our Annual Review focuses on these 3 themes and show you how the top weaknesses NodeZero found and exploited over the past year led to critical impacts, deeper implications, and ultimately positive action by the customer to remediate vulnerabilities and weaknesses. Additionally, the 3 themes presented align with CISA’s Top 15 Routinely Exploited Vulnerabilities list and their Known Exploited Vulnerabilities List (KEVL) catalog. The list below highlights the top 10 vulnerabilities and weaknesses that NodeZero enumerated and exploited over the last year:
1) Credential Policies Are Weak, Or Often Not Enforced
Attackers don’t “hack” in, they log in. Regardless of what the headlines in our newsfeeds may say, cyber threat actors do not often use sophisticated hacking tools and techniques like zero-day exploits to gain access to a network; they simply log in with legitimate user credentials. Our customers are keenly aware of the risks that credential-based attacks pose to their organizations because NodeZero allows them to safely…