New Sysrv Botnet Variant Makes Use of Google Subdomain to Spread XMRig Miner
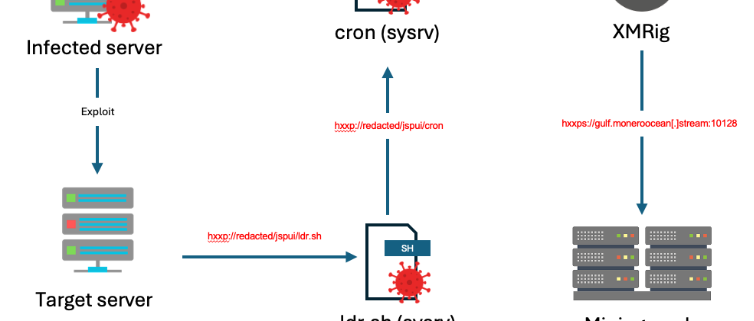
Sysrv is a well-documented botnet first identified in 2020, with the main payload being a worm written in Golang. It drops a cryptominer onto infected hosts before attempting to propagate itself using various methods, including network vulnerabilities. Over the past few years, the botnet has evolved and adapted and has been broadly documented by researchers from various different organizations [1][2][3]. In this blog we will explore the latest variant (shown in the infection chain diagram below), along with the new techniques used, and the latest IoCs uncovered by Imperva Threat Research.
Compromised Sites
Imperva Threat Research first uncovered suspicious behavior relating to the botnet in early March, in the form of blocked HTTP requests observed hitting Imperva proxies. The requests were highly indicative of bot traffic, targeting many sites, across multiple countries. The requests shared common signatures and attempted to exploit multiple known web vulnerabilities in Apache Struts (CVE-2017-9805) and Atlassian Confluence (CVE-2023-22527 and CVE-2021-26084).
A more interesting observation, however, was the use of a seemingly legitimate domain belonging to a known Malaysian academic institution, whose name we have withheld to allow them to remediate the infection. The domain is used to host the institution’s digital archive, and is based on a platform known as Duraspace or DSpace. The perpetrators of this iteration of the sysrv botnet campaign appear to have compromised the site to host their malicious files.
Updated Dropper Script
As part of our analysis of this campaign, we downloaded and analyzed the malware samples hosted on the compromised site. The first of these was a dropper bash script named “ldr.sh”, which is notably similar to previously documented iterations of the sysrv botnet.
The script defines several variables related to the downloading of the second stage binary: the “cc” variable, which contains the URL of the compromised site; a sys variable, which contains a random string generated from the md5 hash of the date; and, a get function, which can be used to download files from URLs passed to it.
The variables and function are used later in the…