10-Year-Old ‘RUBYCARP’ Romanian Hacker Group Surfaces with Botnet
A threat group of suspected Romanian origin called RUBYCARP has been observed maintaining a long-running botnet for carrying out crypto mining, distributed denial-of-service (DDoS), and phishing attacks.
The group, believed to be active for at least 10 years, employs the botnet for financial gain, Sysdig said in a report shared with The Hacker News.
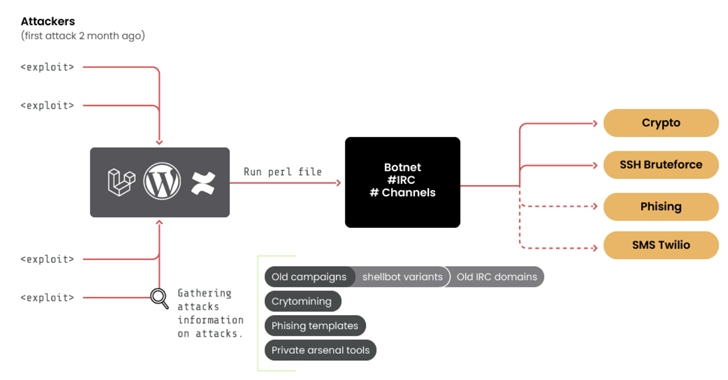
“Its primary method of operation leverages a botnet deployed using a variety of public exploits and brute-force attacks,” the cloud security firm said. “This group communicates via public and private IRC networks.”
Evidence gathered so far suggests that RUBYCARP may have crossover with another threat cluster tracked by Albanian cybersecurity firm Alphatechs under the moniker Outlaw, which has a history of conducting crypto mining and brute-force attacks and has since pivoted to phishing and spear-phishing campaigns to cast a wide net.
“These phishing emails often lure victims into revealing sensitive information, such as login credentials or financial details,” security researcher Brenton Isufi said in a report published in late December 2023.
A notable aspect of RUBYCARP’s tradecraft is the use of a malware called ShellBot (aka PerlBot) to breach target environments. It has also been observed exploiting security flaws in the Laravel Framework (e.g., CVE-2021-3129), a technique also adopted by other threat actors like AndroxGh0st.
In a sign that the attackers are expanding their arsenal of initial access methods to expand the scale of the botnet, Sysdig said it discovered signs of WordPress sites being compromised using commonly used usernames and passwords.
“Once access is obtained, a backdoor is installed based on the popular Perl ShellBot,” the company said. “The victim’s server is then connected to an [Internet Relay Chat] server acting as command-and-control, and joins the larger botnet.”
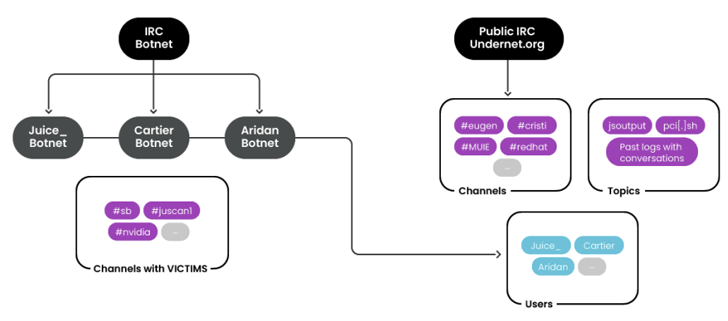
The botnet is estimated to comprise over 600 hosts, with the IRC server (“chat.juicessh[.]pro”) created on May 1, 2023. It heavily relies on IRC for general communications as well as for managing its botnets and coordinating crypto mining campaigns.
Furthermore, members of the group – named…