New XLoader botnet uses probability theory to hide its servers

Threat analysts have spotted a new version of the XLoader botnet malware that uses probability theory to hide its command and control servers, making it difficult to disrupt the malware’s operation.
This helps the malware operators continue using the same infrastructure without the risk of losing nodes due to blocks on identified IP addresses while also reducing the chances of being tracked and identified.
XLoader is an information-stealer that was originally based on Formbook, targeting Windows and macOS operating systems. It first entered widespread deployment in January 2021.
Researchers at Check Point, who have been following the evolution of the malware, have sampled and analyzed the more recent XLoader versions 2.5 and 2.6 and spotted some critical differences compared to previous versions.
Law of large numbers
XLoader already camouflaged its actual command and control (C2) servers in version 2.3 by hiding the real domain name in a configuration that includes 63 decoys.
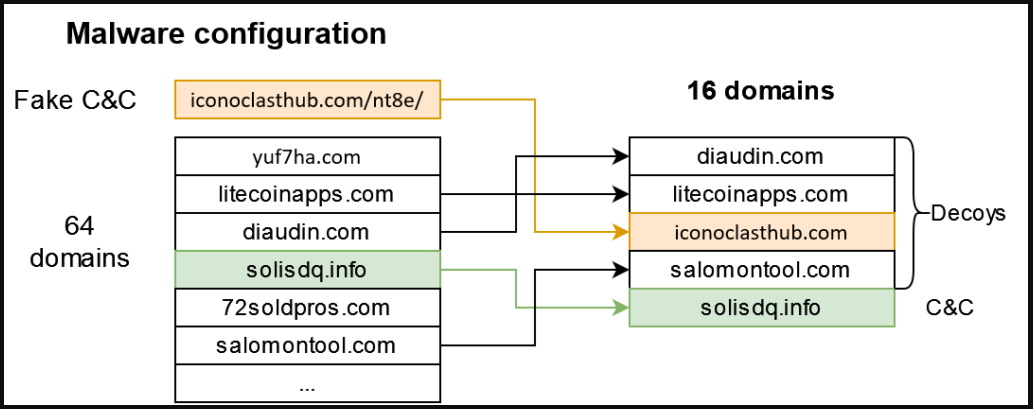
In the most recent versions, though, Check Point’s analysts noticed that the malware overwrites 8 out of a list of randomly chosen domains from the 64 in its configuration list with new values in every communication attempt.
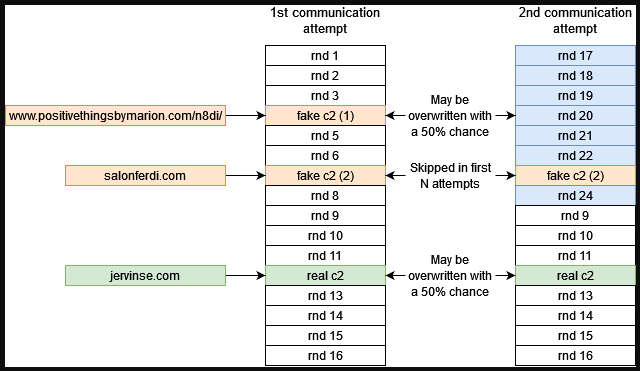
“If the real C&C domain appears in the second part of the list, it is accessed in every cycle once in approximately every 80-90 seconds. If it appears in the first part of the list, it will be overwritten by another random domain name,” explains CheckPoint.
“The eight domains that overwrite the first part of the list are chosen randomly, and the real C&C domain might be one of them. In this case, the probability that a real C&C server will be accessed in the next cycle is 7/64 or 1/8 depending on the position of the “fake c2 (2)” domain.”
This helps in disguising the real C2 servers from security analysts while keeping the impact on the malware’s operations at a minimum.
Successful C2 access results from the law of large numbers, which increases the probabilities of obtaining the expected outcome given enough trials.
As CheckPoint explains via the following…