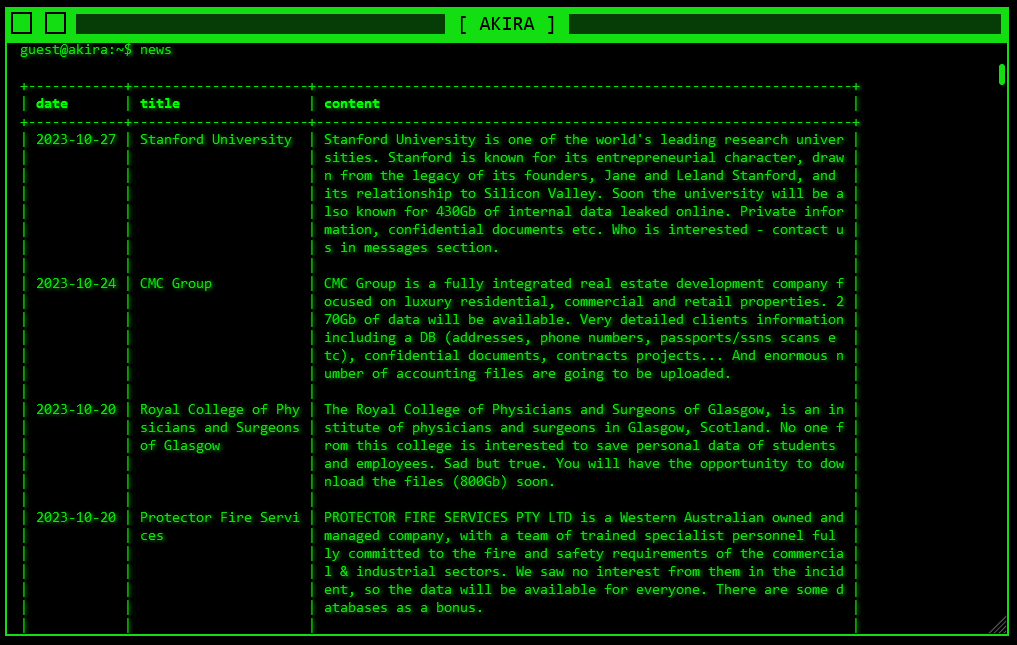
New Ransomware Actor Threatens Change Healthcare
UnitedHealth Group’s Change Healthcare is facing a second extortion demand following a February ransomware attack that sent shockwaves across the sector.
When the cyber crime group BlackCat first hit the health technology and payments processing giant, the effects left patients struggling to get care and health-care providers struggling to stay afloat financially. Change Healthcare reportedly paid off the ransomware attackers in March, but now the company must decide how to respond to claims from another ransomware group, RansomHub, which says it has 4 TB of stolen data, per The Register.
That data allegedly includes personally identifying information on patients and active military personnel, as well as medical and dental records, payments and claims information and source code files for Change Healthcare software solutions, per SC Media.
Researchers have posed several theories on how RansomHub could have gotten this data, if its claims are true.
Some suggest BlackCat may have reformed under a new name and is seeking a second payout. Others suggest that former BlackCat affiliates — stiffed by BlackCat developers on their share of the original extortion — held onto the stolen data and joined up with RansomHub, The Register reports. A conversation posted by a malware resource sharing group, if genuine, adds some weight to the latter theory, per SC Media.
Possibly, RansomHub could have separately compromised Change Healthcare. A researcher told SC Media that it is not uncommon for responders to a cyber incident to discover several threats inside a victim’s compromised environment.
Records of blockchain transactions linked to BlackCat, as well as claims on criminal forums, suggest Change Healthcare made a $22 million payment to the ransomware gang, although the company has not confirmed.
BlackCat operated with a ransomware-as-a-service model, in which developers create malicious code and affiliates then gain access to victim networks and deploy that ransomware. If victims pay, developers and affiliates each take cuts of the earnings.
In the case of Change Healthcare, however, BlackCat may have made off with the…