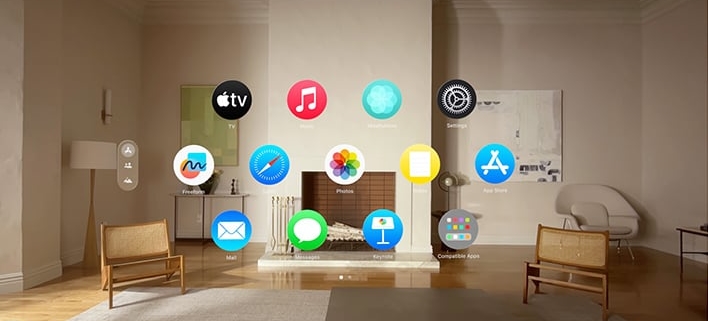
Apple Rushes To Fix A Vision Pro Zero Day Exploit, Announces 600 Apps For Today’s Launch
With gaming, there is a plethora of opportunity here for Apple to expand on the popularity of Apple Arcade, and gain some high-end marketshare on that front from other popular headsets.
Productivity is a major area where Apple plans to focus its efforts, with the idea that spatial computing can replace the traditional desktop for some users. Apps such as Zoom, popular with work-from-home, can be a starting point for those dipping their feet into this immersive world that Apple is aiming for.
If users will ultimately buy into the idea of Vision Pro as a replacement or supplemental device for work and play remains to be seen. While there is no killer app available yet, the Apple ecosystem is robust and the technology is sufficiently capable to provide an experience not available elsewhere yet.
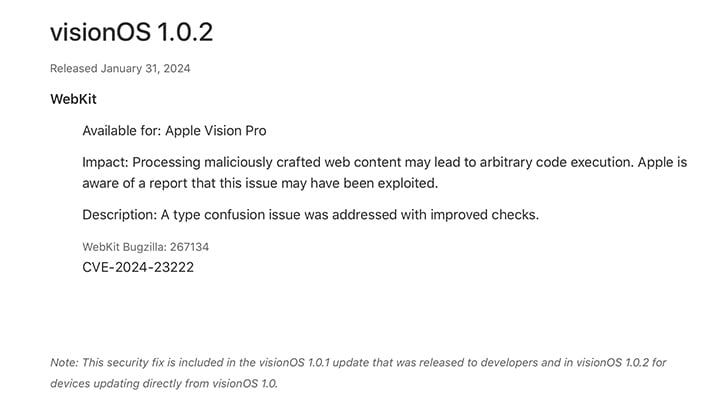
While Vision Pro won’t have the same number of users as Apple’s iPhone, there will be a sufficient user base that makes security updates like this vital. Apple products have a reputation for being less likely to have issues such as malware, so keeping that reputation on a halo product such as Vision Pro is certainly in Apple’s best interest.