US reveals bespoke tool that took down Russian malware operation
Image: Getty via Dennis
The US Department of Justice (DoJ) has revealed details of a joint operation in which Western agencies used a custom tool to destroy a decades-old Russian malware operation.
Use of a tool named PERSEUS nullified a worldwide network of devices that had been infected with the Snake malware by threat actors in the group Turla.
A number of agencies including the NSA, FBI, and the Cybersecurity and Infrastructure Security Agency (CISA) led the operation codenamed Medusa.
![]()

Snake had been used to exfiltrate sensitive information from devices across 50 or more countries, including NATO governments and journalists, but the FBI-created PERSEUS was used to force the malware to overwrite its data without damaging infected devices.
Turla has been linked directly with the Federal Security Service of the Russian Federation (FSB) and has used Snake since 2003.
“For 20 years, the FSB has relied on the Snake malware to conduct cyber espionage against the United States and our allies – that ends today,” said Matthew G. Olsen, assistant attorney general, at the Justice Department’s National Security Division.
“The Justice Department will use every weapon in our arsenal to combat Russia’s malicious cyber activity, including neutralising malware through high-tech operations, making innovative use of legal authorities, and working with international allies and private sector partners to amplify our collective impact.”
Snake is able to function on Windows, macOS, and Linux under a high level of stealth, and has been operated in a…
FBI says it has sabotaged hacking tool created by Russia’s elite spies
Experts disabled the ‘Snake’ malware used by the FSB against US computers, in what could be a death blow to one of Moscow’s leading cyber espionage programs.
FBI says it has sabotaged hacking tool created by elite Russian spies
WASHINGTON :The FBI has sabotaged a suite of malicious software used by elite Russian spies, U.S. authorities said on Tuesday, providing a glimpse of the digital tug-of-war between two cyber superpowers.
Senior law enforcement officials said FBI technical experts had identified and disabled malware wielded by Russia’s FSB security service against an undisclosed number of American computers, a move they hoped would deal a death blow to one of Russia’s leading cyber spying programs.
“We assess this as being their premier espionage tool,” one of the U.S. officials told journalists ahead of the release. He said Washington hoped the operation would “eradicate it from the virtual battlefield.”
The official said the FSB spies behind the malware, known as Snake, are part of a notorious hacking group tracked by the private sector and known as “Turla.”
The group has been active for two decades against a variety of NATO-aligned targets, U.S. government agencies and technology companies, a senior FBI official said.
Russian diplomats did not immediately return a message seeking comment. Moscow routinely denies carrying out cyberespionage operations.
U.S. officials spoke to journalists on Tuesday ahead of the news release on condition that they not be named. Similar announcements, revealing the FSB cyber disruption effort, were made by security agencies in the UK, Canada, Australia and New Zealand.
Turla is widely considered one of the most sophisticated hacking teams studied by the security research community.
“They have persisted in the shadows by focusing on stealth and operational security,” said John Hultquist, vice president of threat analysis at U.S. cybersecurity company Mandiant. “They are one of the hardest targets we have.”
The U.S. government dubbed the disruption of Turla’s Snake malware “Operation Medusa.” The FBI and its partners identified where the hacking tool had been deployed across the internet and built a unique software “payload” to disrupt the hackers’ infrastructure.
The FBI relied on existing search warrant authorities to remotely access the Russian malicious program within victim networks in the U.S. and sever its connections.
The senior FBI official said the Bureau’s…
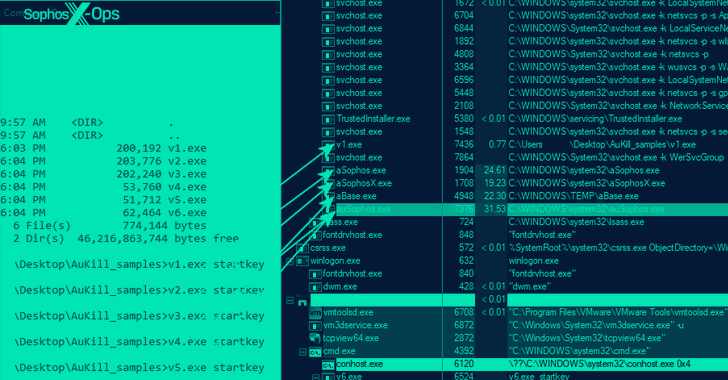
Ransomware Hackers Using AuKill Tool to Disable EDR Software Using BYOVD Attack
Threat actors are employing a previously undocumented “defense evasion tool” dubbed AuKill that’s designed to disable endpoint detection and response (EDR) software by means of a Bring Your Own Vulnerable Driver (BYOVD) attack.
“The AuKill tool abuses an outdated version of the driver used by version 16.32 of the Microsoft utility, Process Explorer, to disable EDR processes before deploying either a backdoor or ransomware on the target system,” Sophos researcher Andreas Klopsch said in a report published last week.
Incidents analyzed by the cybersecurity firm show the use of AuKill since the start of 2023 to deploy various ransomware strains such as Medusa Locker and LockBit. Six different versions of the malware have been identified to date. The oldest AuKill sample features a November 2022 compilation timestamp.
The BYOVD technique relies on threat actors misusing a legitimate, but out-of-date and exploitable, driver signed by Microsoft (or using a stolen or leaked certificate) to gain elevated privileges and turn off security mechanisms.
By using legitimate, exploitable drivers, the idea is to bypass a key Windows safeguard known as Driver Signature Enforcement that ensures kernel-mode drivers have been signed by a valid code signing authority before they are allowed to run.
“The AuKill tool requires administrative privileges to work, but it cannot give the attacker those privileges,” Sophos researchers noted. “The threat actors using AuKill took advantage of existing privileges during the attacks, when they gained them through other means.”
This is not the first time the Microsoft-signed Process Explorer driver has been weaponized in attacks. In November 2022, Sophos also detailed LockBit affiliates’ use of an open source tool called Backstab that abused outdated versions of the driver to terminate protected anti-malware processes.
Then earlier this year, a malvertising campaign was spotted utilizing the same driver to distribute a .NET loader named MalVirt to deploy the FormBook information-stealing malware.
The development comes as the AhnLab Security Emergency response Center (ASEC) revealed that poorly managed…