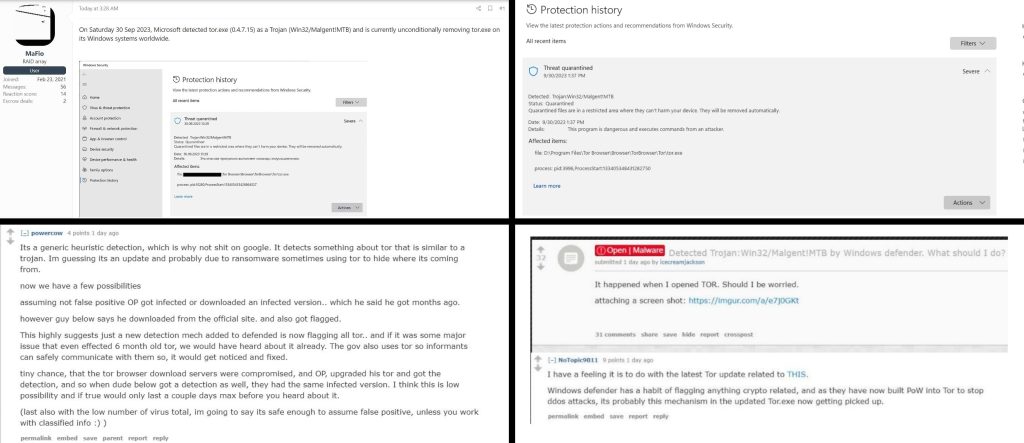
Microsoft Defender Flags Tor Browser as Win32/Malgent!MTB Malware
The detection of Tor browser’s latest version as Win32/Malgent!MTB malware is likely a false positive.
Microsoft Defender, a popular antivirus program, is apparently falsely flagging Tor Browser as Win32/Malgent!MTB malware. This is causing concern for users who rely on the Tor Browser to protect their privacy and security.
Tor Browser is a free and open-source web browser that uses the Tor network to anonymize browsing traffic. This makes it a popular choice for users who want to protect their privacy online.
Microsoft Defender is detecting the latest version of Tor Browser as malware because it is using a new heuristic detection method that is designed to identify Trojans that use Tor to hide their activity. However, the heuristic method is too broad and also flags the Tor Browser itself as malware.
What is the heuristic detection method?
Heuristic detection is a method of detecting malware that uses rules and algorithms to identify suspicious behaviour. It is different from signature-based detection, which relies on a database of known malware signatures.
Heuristic detection methods can be very effective at detecting new and emerging malware threats, but they can also generate false positives. This is because heuristic detection methods can sometimes flag benign software as malware.
According to Microsoft, its Defender security solution uses a combination of signature-based and heuristic detection methods to protect users from malware. However, the recent false positive detections of Tor Browser suggest that the heuristic detection method in Microsoft Defender may be too broad.
Win32 Malgent!MTB malware?
Win32/Malgent!MTB is a generic detection that Microsoft Defender uses to identify Trojans that are designed to perform a variety of malicious actions on a computer.
These actions can include downloading and installing other malware, using the computer for click fraud, recording keystrokes and the websites visited, sending information about…