Raspberry Robin Malware Upgrades with Discord Spread and New Exploits
The operators of Raspberry Robin are now using two new one-day exploits to achieve local privilege escalation, even as the malware continues to be refined and improved to make it stealthier than before.
This means that “Raspberry Robin has access to an exploit seller or its authors develop the exploits themselves in a short period of time,” Check Point said in a report this week.
Raspberry Robin (aka QNAP worm), first documented in 2021, is an evasive malware family that’s known to act as one of the top initial access facilitators for other malicious payloads, including ransomware.
Attributed to a threat actor named Storm-0856 (previously DEV-0856), it’s propagated via several entry vectors, including infected USB drives, with Microsoft describing it as part of a “complex and interconnected malware ecosystem” with ties to other e-crime groups like Evil Corp, Silence, and TA505.
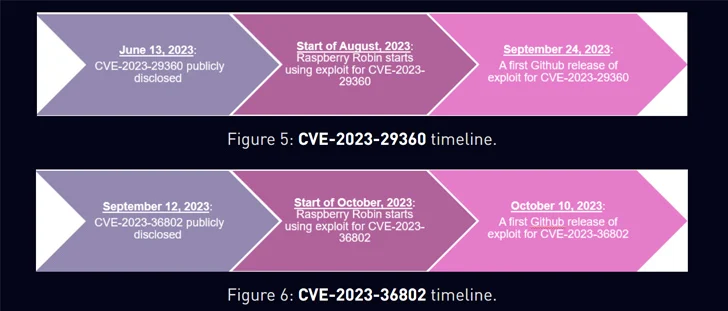
Raspberry Robin’s use of one-day exploits such as CVE-2020-1054 and CVE-2021-1732 for privilege escalation was previously highlighted by Check Point in April 2023.
The cybersecurity firm, which detected “large waves of attacks” since October 2023, said the threat actors have implemented additional anti-analysis and obfuscation techniques to make it harder to detect and analyze.
“Most importantly, Raspberry Robin continues to use different exploits for vulnerabilities either before or only a short time after they were publicly disclosed,” it noted.
“Those one-day exploits were not publicly disclosed at the time of their use. An exploit for one of the vulnerabilities, CVE-2023-36802, was also used in the wild as a zero-day and was sold on the dark web.”
A report from Cyfirma late last year revealed that an exploit for CVE-2023-36802 was being advertised on dark web forums in February 2023. This was seven months before Microsoft and CISA released an advisory on active exploitation. It was patched by the Windows maker in September 2023.
Raspberry Robin is said to have started utilizing an exploit for the flaw sometime in October 2023, the same month a public exploit code was made available, as well as for CVE-2023-29360 in August. The latter was publicly…