Ransomware Leak Site Victims Reached Record-High in November
After a quieter month in October, ransomware groups seemed to return with a vengeance in November, with the highest number of listed victims ever recorded, according to Corvus Insurance.
In a report published on December 18, 2023, Corvus Threat Intel observed 484 new ransomware victims posted to leak sites in November.
This represents a 39.08% increase from October and a 110.43% increase compared with November 2022.
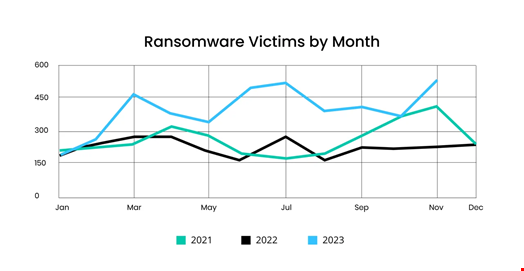
This is the eleventh month in a row with a year-on-year increase in ransomware victims and the ninth in a row with victim counts above 300. This is also the third time such a record has been broken this year.
However, while the previous two records in 2023 were primarily attributed to Clop’s MOVEit supply chain attack, this was not the case in November.
A CitrixBleed-Induced LockBit’s Activity Peak
According to Corvus’ data, the November peak was partly due to a resurgence in LockBit’s activity.
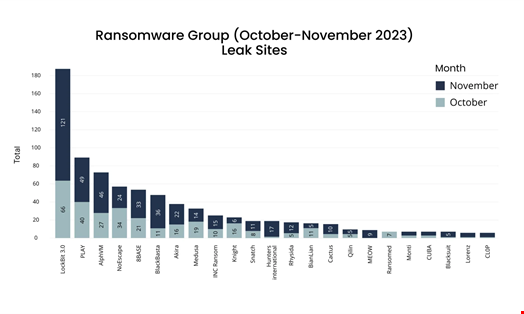
November was LockBit’s third-highest month of 2023 in terms of listed victims (121) after a quieter Fall.
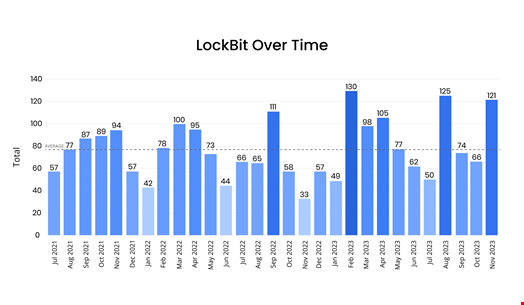
If the first two peaks were due to affiliates returning to work after a winter or a summer break, Corvus threat intelligence analysts estimated that the November increase could be attributed to the CitrixBleed vulnerability, “which has reportedly become a new staple for the group.”
Read more: LockBit Affiliates are Exploiting Citrix Bleed, Government Agencies Warn
Could QakBot Resurgence Mean a New Record this Winter?
Based on historical seasonal data, the Corvus Threat Intel team predicted that the number of ransomware leak site victims listed in December will be higher than in December 2022 but likely won’t match November’s numbers.
“We expect a decrease in January as the humans behind ransomware attacks take some time off,” the researchers added.
Finally, Corvus observed that although the take-down of malware loader QakBot (aka QBot) by law enforcement in August impacted ransomware groups. This new resurgence in victim listings showed that “the ransomware ecosystem has successfully pivoted away from QBot.”
The fact that…




