Hackers Don’t Even Have To Hack Users Who Voluntarily Download Apps And Browser Extensions
I previously wrote What Do Hacking And Malware Have To Do With Ad Fraud? Put simply, hackers get malware onto devices not only to collect personal information and steal passwords from real human users. They also use the malware to make money via ad fraud. Monetizing via ad fraud is more efficient and profitable than harvesting passwords for sale on the dark web. The former is a one-step process that yields continuous high-margin profits; the latter is a two-step process, and the hacker is not even sure if there will be buyers for his lists of compromised passwords. In recent years, we’ve seen hackers dump entire datafiles of passwords for free on hacker forums. This suggests they could not even find any buyer for that data, because it is already so prevalent and readily available. So hackers are increasingly using their malware and botnets for digital ad fraud instead – loading ads and website pages in the background to make money.
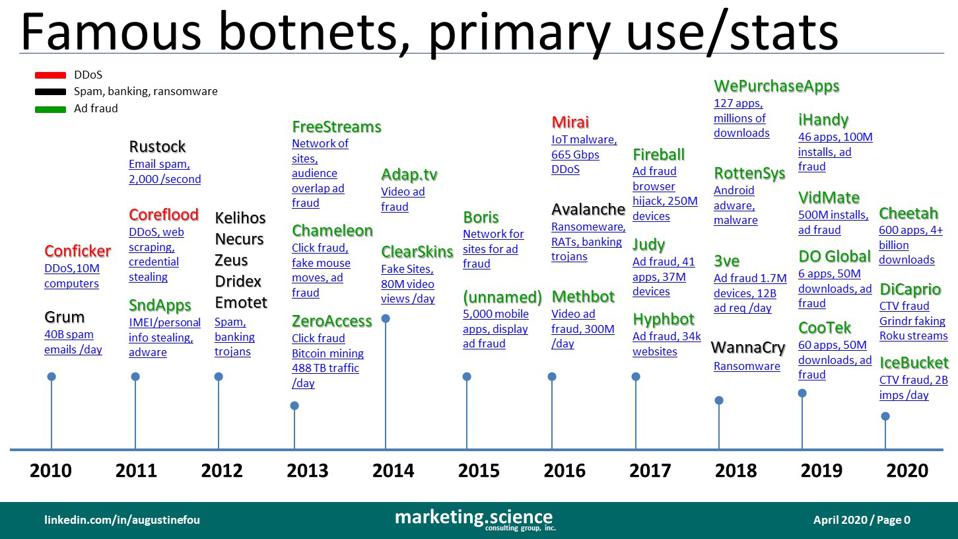
Note that more and more of the recent botnets are colored green, which means their primary use is ad fraud, as opposed to DDoS (distributed denial of service) attacks, spam, or ransomware.
Augustine Fou
No Hacking Needed
But hackers may not even need to spend any effort hacking into real humans’ devices. In some cases, unsuspecting humans voluntarily download browser extensions or mobile apps that are already laced with malicious code. The code is designed to load ads in the background even when the app is not in use or the mobile device is not in use. This is ad fraud because the millions of ad impressions are never seen by human users. Today comes yet another story of humans downloading browser extensions that purport to do one thing, but in actuality are designed for committing ad fraud in the background.
“The 28 extensions contained code that could perform several malicious operations. Avast said it found code to:
- redirect user traffic to ads
- redirect user traffic to phishing sites
- collect personal data, such as birth dates, email addresses, and active devices
- collect browsing history
- download further malware onto a user’s device
…
