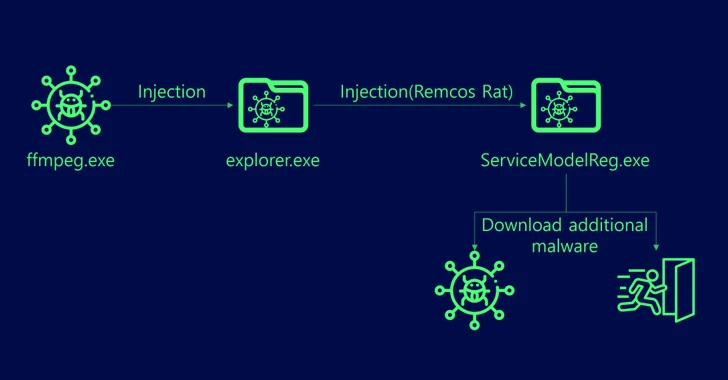
Palo Alto’s Unit 42 team reveals new wave of PAN-OS firewall hack attempts
PAN-OS firewalls are facing an “increasing number of attacks”, though so far, signs of active command execution are rare.
Palo Alto’s PAN-OS firewalls are coming under increasing attack following the company’s disclosure of a command injection vulnerability on 12 April.
A few days later, the Australian Signals Directorate’s Australian Cyber Security Centre circulated a critical alert over the vulnerability, warning Australian organisations using Palo Alto’s firewalls to “act now” to mitigate the vulnerability, while Palo Alto said it was working on a hotfix.
Now, Palo Alto’s Unit 42 has shared more details of how the vulnerability – CVE-2024-3400, which could allow a threat actor to run arbitrary code on affected PAN-OS firewalls – is being actively exploited.
The big brains at Unit 42 have broken down the exploitation attempts into four discrete groups.
At level zero, we have threat actors simply probing customer networks and failing to make any kind of access. Unit 42 expected these attempts to have “little to no immediate impact” on organisations, and simply applying the available hotfix should remedy the situation.
Unit 42 rates level one as threat actors actively testing the vulnerability. In this case, “a zero-byte file has been created and is resident on the firewall. However, there is no indication of any known unauthorised command execution.”
Again, applying Palo Alto’s hotfix should do the trick.
In both cases, Unit 42 believes resetting the impacted device is unnecessary, as there is no indication of active compromise or data exfiltration.
At level two, however, Unit 42 is beginning to see “potential exfiltration” of data.
“A file on the device has been copied to a location accessible via a web request, though the file may or may not have been subsequently downloaded,” Unit 42 said in a blog post. “Typically, the file we have observed being copied is running_config.xml.”
Unit 42’s advice in this case is to both install the hotfix and perform a private data reset.
“Private data reset clears all logs and reverts the configuration to factory defaults,” Unit 42 said. “The system will restart…