Who’s Behind the 8Base Ransomware Website? – Krebs on Security
The victim shaming website operated by the cybercriminals behind 8Base — currently one of the more active ransomware groups — was until earlier today leaking quite a bit of information that the crime group probably did not intend to be made public. The leaked data suggests that at least some of website’s code was written by a 36-year-old programmer residing in the capital city of Moldova.

The 8Base ransomware group’s victim shaming website on the darknet.
8Base maintains a darknet website that is only reachable via Tor, a freely available global anonymity network. The site lists hundreds of victim organizations and companies — all allegedly hacking victims that refused to pay a ransom to keep their stolen data from being published.
The 8Base darknet site also has a built-in chat feature, presumably so that 8Base victims can communicate and negotiate with their extortionists. This chat feature, which runs on the Laravel web application framework, works fine as long as you are *sending* information to the site (i.e., by making a “POST” request).
However, if one were to try to fetch data from the same chat service (i.e., by making a “GET” request), the website until quite recently generated an extremely verbose error message:
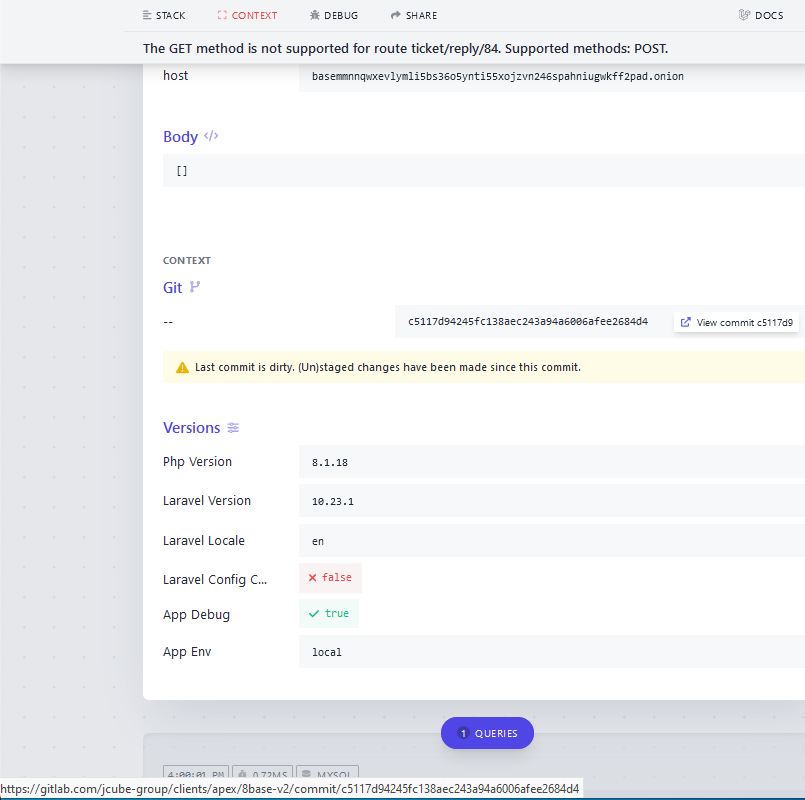
The verbose error message when one tries to pull data from 8Base’s darknet site. Notice the link at the bottom of this image, which is generated when one hovers over the “View commit” message under the “Git” heading.
That error page revealed the true Internet address of the Tor hidden service that houses the 8Base website: 95.216.51[.]74, which according to DomainTools.com is a server in Finland that is tied to the Germany-based hosting giant Hetzner.
But that’s not the interesting part: Scrolling down the lengthy error message, we can see a link to a private Gitlab server called Jcube-group: gitlab[.]com/jcube-group/clients/apex/8base-v2. Digging further into this Gitlab account, we can find some curious data points available in the JCube Group’s public code repository.
For example, this “status.php” page, which was committed to JCube Group’s Gitlab repository roughly one month ago, includes code that makes…