Ziggy Ransomware Crew Quits Business, Refunds Victims’ Stolen Money
The Ziggy ransomware crew, which ostensibly quit the business in early February 2021 over a fit of remorse, said it will return to their victims the money they’ve extorted merely for an email containing proof of payment.
So, if you’ve paid the cyber crime perps any money in a ransom ploy just calculate the amount in Bitcoin and the computer ID and your money will be shuttled off to the Bitcoin wallet in about two weeks, said Ziggy’s admin, who reportedly has spoken with ThreatPost and BleepingComputer. Bitcoin value on the day of payment would be the basis to calculate the refund.
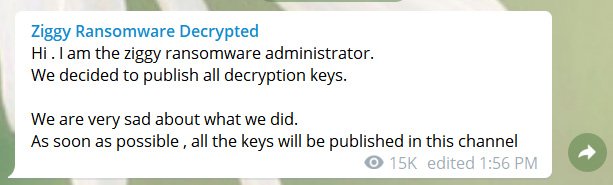
The Ziggies apparently feared law endorsement repercussions if they continued their cyber kidnappings, the Ziggy rep told Threatpost. “Hello dear. Yes, I’m Ziggy ransomware developer. We decided to return victims’ money because we fear law enforcement action,” the person told Threatpost.
They have a point. In January 2021, international law enforcement and judicial authorities in eight countries dismantled the Emotet botnet, widely regarded as the world’s most dangerous and notorious malware operation, taking it down from the inside by redirecting hundreds of infected machines to a law enforcement environment.
At the same time, the U.S. Justice Department said it had hit the NetWalker ransomware syndicate, which operates as a ransomware-as-a-service model, by seizing nearly $500,000 in cryptocurrency from ransom payments and disabling a dark web hidden resource used to communicate with the gang’s victims. Ziggy’s withdrawal amounts to a victory for law enforcement, which has repeatedly said that an accumulation of indictments and actions to gut hackers’ infrastructure would discourage further attacks.
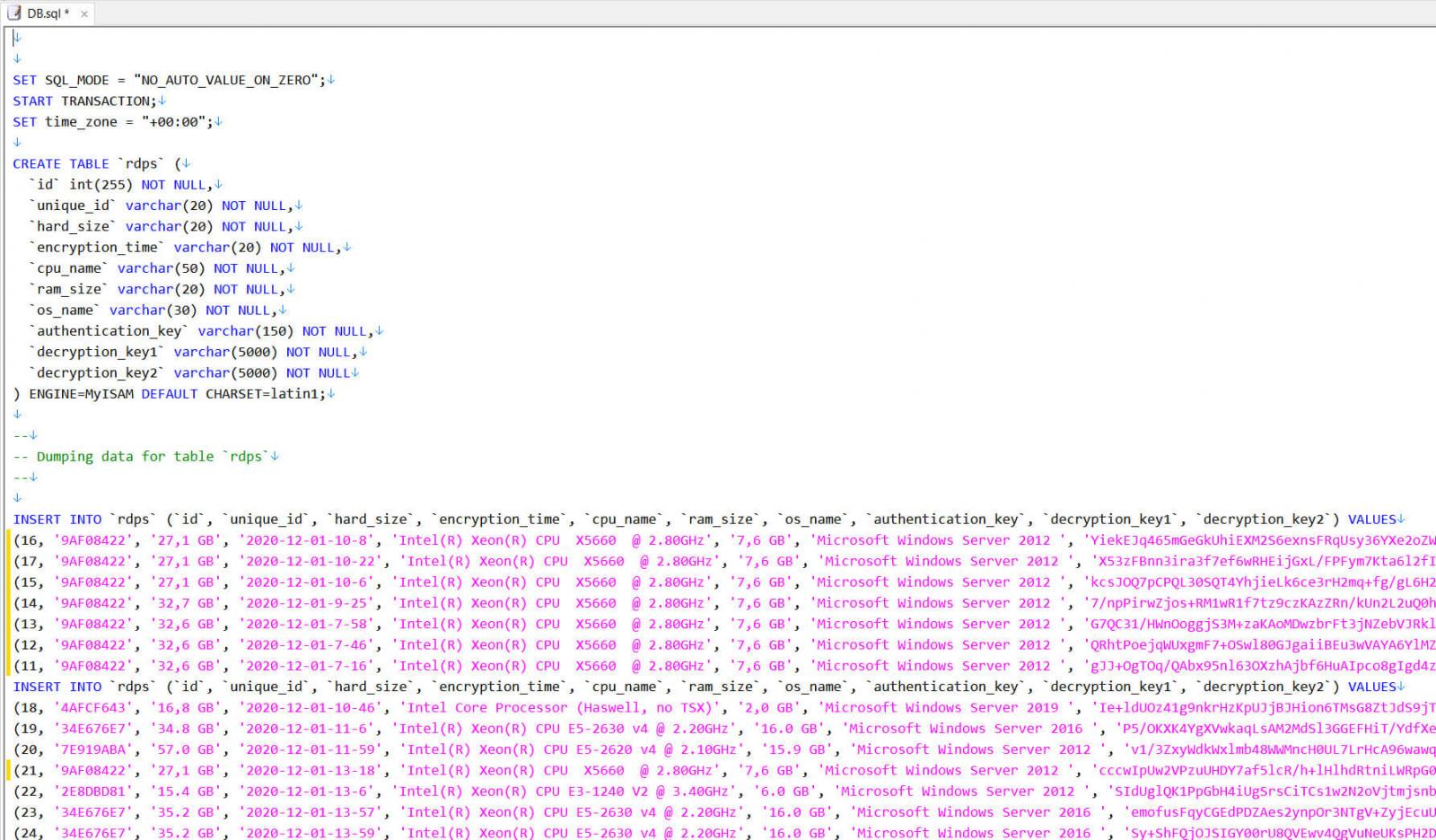
Ziggy reportedly propagated garden variety ransomware, picking on computers to encrypt files and then demanding a sum of money to reverse their handiwork. The cyber kidnappers evidently didn’t steal files. According to Threatpost, Ziggy has released more than 900 decryption keys, which will unlock the victims’ files. There’s a bit of a catch to the whole thing. Using the sullied money, Ziggy made a couple of bucks. When Ziggy released…