Top three most critical areas of web security
Akamai Technologies revealed three research reports at the RSA Conference 2022, focusing on three of the most critical areas of web security: ransomware, web applications and APIs, and DNS traffic.
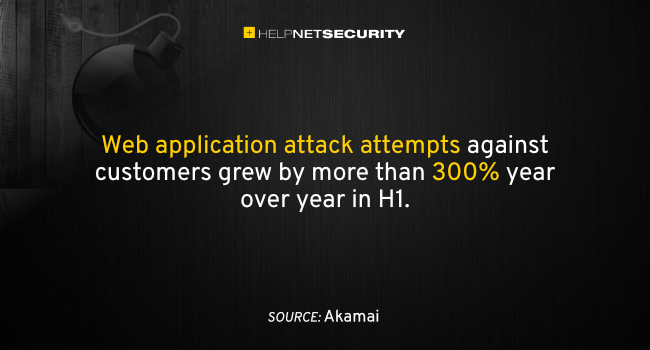
Analyzing trillions of data points across its multiple platforms, the research team uncovered new findings on threat actor behavior via popular attack traffic and techniques. The three reports link the most prominent security trends and paint an accurate map of the modern attack landscape.
An up-to-date analysis of ransomware attack trends highlight the risks and suggest mitigation, while an analysis of Web app and API attack trends offers a fresh look at the infection vectors used by ransomware operators and others. An analysis of DNS complements the reports with a view of overall attacks analyzed via one of the internet’s most foundational technologies.
The analysis centers on attack trends and techniques as well as solutions to solve today’s most pressing cybersecurity issues.
Highlights from each report
Ransomware threat
With the rise of Ransomware-as-a-Service (RaaS) attacks, including from the Conti ransomware gang, Akamai analyzed and discovered the most recent and effective components of ransomware attackers’ methodologies, tools and techniques. Key findings include:
- Sixty percent of successful Conti attacks were conducted on United States companies, while 30% occurred in the European Union.
- An analysis of the industries attacked highlights the risk of supply chain disruption, critical infrastructure impact, and supply chain cyberattacks.
- Most successful Conti attacks target businesses with $10-250 million in revenue, indicating a “goldilocks” range of successful attack targets among medium and small businesses.
- The gang’s tactics, techniques, and procedures (TTPs) are well-known, but highly effective – a sobering reminder of the arsenal that is at the disposal of other hackers. But also that these attacks can be prevented with the right mitigation.
- Conti’s emphasis in their documentation on hacking and hands-on propagation, rather than encryption, should drive network defenders to focus on those parts of the kill chain as well, instead of focusing…


